The Razer synapse zero-day vulnerability has been revealed on Twitter, permitting you to achieve Windows admin rights just by plugging in a Razer mouse or a keyboard.
Razer is one of the well-known computer peripherals manufacturers also know for its gaming mouse and keyboards. When plugging in a Razer peripheral in to Windows 10 or Windows 11, the operating system will automatically download and start installing the Razer Synapse software on your system. Razer Synapse is software that permits users to configure their hardware devices, set up map buttons, or macros.
Razer states that their Razer Synapse software is utilized by more than 100 million users across the world. Our security researchers also founded a zero-day vulnerability in the plug-and-play Razer Synapse installation that permits the users to achieve all the SYSTEM privileges on a Windows device very quickly.
SYSTEM privileges are the topmost user rights accessible in Windows and permit someone to execute any command on the operating system. Importantly, if any user achieves SYSTEM privileges in Windows, they gain complete control over the system and can install whatever they want, including malware.
After not receiving a response from Razer, a security researcher disclosed the zero-day vulnerability on Twitter and explained how the bug works with a short video.
Achieving SYSTEM Privileges Just by Plugging in a Mouse
Our experts decided to test out the vulnerability and have confirmed that it took them only two minutes to achieve the SYSTEM privileges in Windows 10 right after plugging in our mouse.
It should be recognized that this is a local privilege escalation (LPE) vulnerability, which means that you require having a Razer device and physical access to a computer. With that said, the bug is so easy to exploit as you just require to spend $20 on Amazon for a Razer mouse and plug it into Windows 10 to become an admin. To test this bug, our experts created a temporary ‘Test’ user on one of our Windows 10 computers with standard, non-administrator privileges, as shown below:

While plugging the Razer device into Windows 10, the OS download and install the driver by its own and the Razer Synapse software. When the Razer Synapse software is installed, the setup wizard permits you to specify the folder where you want to install it. The ability to select your installation folder is where everything goes wrong.

When you change the location of your folder, a ‘Choose a Folder dialog will appear. If you press Shift and right-click on the dialog, you will be indicated to launch the ‘Open PowerShell window here,’ which will launch a PowerShell prompt in the folder shown in the dialog.
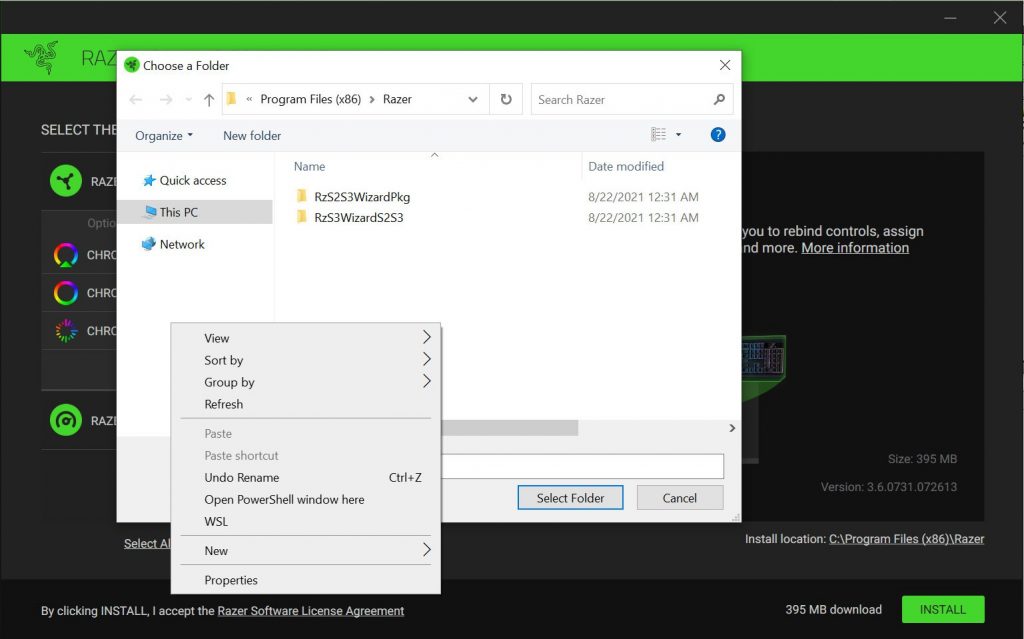
After this PowerShell prompt is being opened by a process with SYSTEM privileges, the PowerShell prompt will also acquire those same privileges.
As you can see below, after we launched the PowerShell prompt and typed the ‘whom command, it showed that the console has SYSTEM privileges permitting us to issue any command we want.

How does Razer fix the Vulnerability?
After the zero-day vulnerability achieved broad attention on Twitter, Razer has contacted the security researcher to let them know that they will be issuing a fix soon.
Razer also told the researcher that he would be receiving a flaw bounty reward even though the vulnerability was publicly disclosed.



