Cybersecurity investigators have discovered a new backdoor operation efficient of stealing user login information, device information and running arbitrary commands on Linux systems.
The trojan dropper has been transformed “Facefish” by the Qihoo 360 Security team having its effectiveness to deliver various rootkits at different times and the use of Blowfish cipher to encode transmissions to the attacker-controlled server.
The researchers said that “Facefish includes 2 parts, Dropper and Rootkit, and its main purpose is to regulated by the Rootkit module, which processes at the Ring 3 layers and is loaded using the LD_PRELOAD feature to thieve user login information by fixing ssh/sshd program related functions, and it also supports some of the backdoor functionalities.”
The Security researchers assemble on a previous analysis, which documented an attack chain targeting Control Web Panel (CWP, formerly CentOS Web Panel) to infuse an SSH embed with data eliminated effectiveness.
How the FaceFish Works?
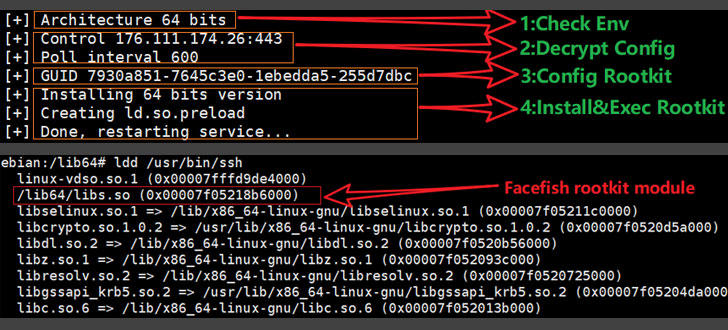
Facefish passes through a multi-stage infection process, which launches with a command injection against CWP to restore a dropper (“sshins”) from a remote server, which then release a rootkit that conclusively takes the initiative of collecting and transmitting all the crucial information back to the server, in addition, to await more instructions issued by the command-and-control (C2) server.
Whereas the identical susceptibility oppressed by the threat actor for start compromise remains unclear, experts noted that CWP has been afflicted by dozens of security concerns, adding the “voluntary encryption and obfuscation” of the original code has made it “challenging to determine which versions of CWP are or remain susceptible to this attack.”
Dropper arrives with its own set of activities to do, chief among actually detecting the runtime environment, decoding a configuration file to get C2 data, configuring the rootkit, and initializing the rootkit by inserting it into the secure shell server process (sshd).
Rootkits are especially threatening as they permit the attacker to access elevated privileges in the device, permitting them to obstruct basic operations managing by the element operating system. The ability of rootkits to mask into the fabric of the operating system provides attackers a high level of stealth and evasion.
Which Transmissions Handled by FaceFish?
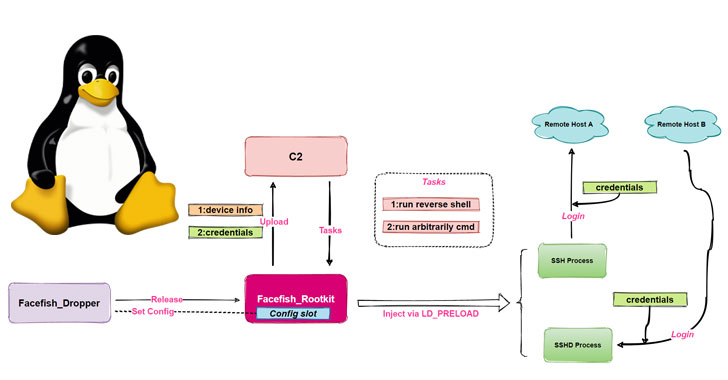
Facefish also handles complicated transmission protocols and encoded algorithms, using the guidance initiating with 0x2XX to transmit public keys and BlowFish for encoded transmission of data with the C2 server. Some of the C2 instructions sent by the server are given below:
- 0x300 – Report swiped sensitive data.
- 0x301 – Retrieve details of the “uname” command.
- 0x302 – Execute reserve shell.
- 0x310 – Run ay system instruction.
- 0x311 – Share the result of bash execution.
- 0x312 – Addressed host information.
Security researchers come from an investigation of an ELF sample file it arrives in February 2021. Some other indicators of negotiates associated with the trojan can be executed here.



