The Trojan Developer discharges their creation on their system to try out the advanced features and the information ended up on a cybercrime intelligence platform, revealing a checkout the cybercriminal endeavor.
The threat actor is the developer of Raccoon, the data hijacked that can gather information from dozens of applications and has been rapidly increasing in popularity for the past two years.
A Name and Email, Still not enough!
While examining an element to the threat actor, the developer of Raccoon harmed their system, a move that urgently triggered the information to pass to the command and control (C2) server and further on, to cybercrime organization.
Raccoon developer’s impacted test system was discovered through Hudson Rock’s Cavalier platform, a cybercrime intelligence database that observes negotiated machines.
Co-Founder and Chief Technology Officer Alon Gal, Hudson Rock, states that Raccoon info stealer impacted their machine in February but went unnoticed because it presented no interest since it was not a machine belonging to the company’s clients.
Alon Gal, Hudson Rock the co-founder and Chief Technology Officer, states that Raccoon info stealer has more than one million negotiated systems that are being monitored through Cavalier.
The researcher told our experts that the developer of Raccoon info stealer abused their machine in February but went unnoticed because it presented no interest since it was not a machine belonging to the company’s clients.
It draws attention through its IP address, 1.1.1.1, modified on purpose in the command and control server so that the real one would not get monitored, Gal says. It is enough, the IP address is used by Cloudflare’s public Domain Name System (DNS) resolver.
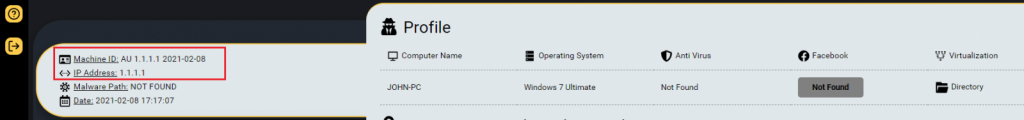
The information gathered from the self-infected system indicates that the developer tested the malware’s ability to extract credentials from Google Chrome, an important attribute for any information stealer. More information dragged from the Raccoon test computer revealed a name and multiple email addresses associated with the malware.
Is the Raccoon Developer Revealed?
Unluckily, the details are insufficient to know the identity of Raccoon’s developer. Gal says that the Trojan creator “likely infected [the machine] on purpose” and was careful enough to remove the details that could reveal who they are before unleashing the malware.
For exemplify, email addresses used for various services contain either “raccoon” or “raccoonstealer,” indicating that they are used for customer communication. The investigators also found the name Benjamin Engel, a threat actor from Berlin and main character in the 2014 German hacker movie “Who Am I.”
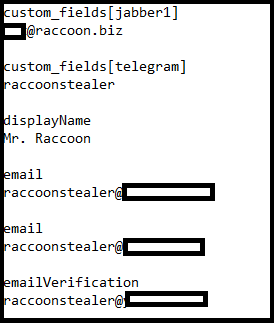
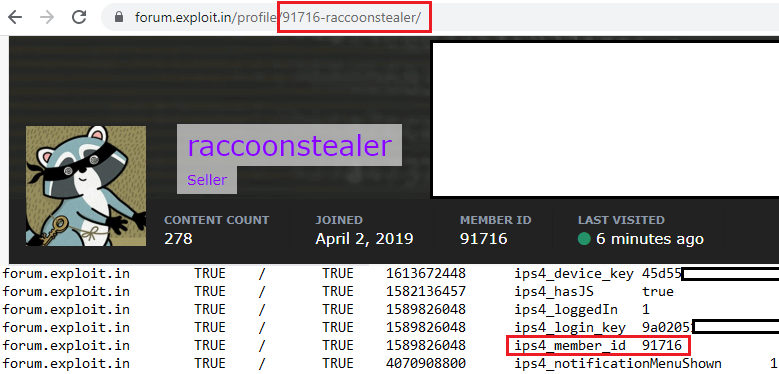
Other information is taken from the test system which indicates that the developer’s test box had cookies indicating logging into a Russian-speaking forum that is popular with prominent cybercriminal groups.
Gal was able to compare the ID in the cookie generated when logging into the forum with the ID attached to the Raccoon stealer account in the community.
While the information gathered this way does not include the hints essentially to put a real name to Raccoon’s developer, it shows that cybercriminals can also slip up and there is still hope to catch them off guard.



