Finally, Microsoft released Sysmon 13 with an updated security feature that is capable to detect if a process is interposed by using process herp derping techniques or hollowing process.
Hackers inject malicious code into an appropriate Window process just to avoid detection by security software. This technique permits the malware to execute, while in Task Manger it displays as a standard Windows process executing in the background.
Hollowing is the process in which malware launches a certain process in a suspended state and exchange certain code in the process with malicious code. After it, this malicious code is executed by the process, with different permissions assigned to that process.
Process her pandering is a more advanced tactic where the malware customizes its image on a hard disk to look similar to legitimate software after the malware loaded. Due to which if the security software scans the on-disk file, it will look like a harmless file while the malicious code is running in the memory.
Multiple malware infections use tempering process to avoid detection that includes Mailto / defray 777 ransomware, Trickbot, and BazarBackdoor.
How to Enable Tampering Process in Sysmon V13?
In case you are not aware of Sysmon, or System Monitor then read this section to know about these processes.
It is a Sysinternals tool that is specially designed to monitor the systems for malicious activities and store logs of those events that are used in the Windows event log.
While enabling the tampering process detection security feature, you need to add the “Process Tampering” configuration option to a file then it will start to monitor basic events that includes the file creation and file time changes without the configuration file.
These new updated features have been added to Sysmon, which can be operated by entering the sysmon -s command.
Now, for enabling the Tampering process you need to execute the configuration file;
<Sysmon schemaversion=”4.50”>
<Event Filtering>
<RuleGroup name=”” groupRelation=”or”>
<ProcessTampering onmatch=”exclude”>
</ProcessTampering>
</RuleGroup>
</EventFiltering>
</Sysmon>
While starting the Sysmon file you need to direct it to the above-configured file, then you need to execute the sysmon-i command it will pass the configuration file name.
Once the execution is started the Sysmon will install its driver and starts collecting the data in the background. It will store the events in a log file named
“Application and Services Logs/ Microsoft/Windows/Sysmon/Operational”.
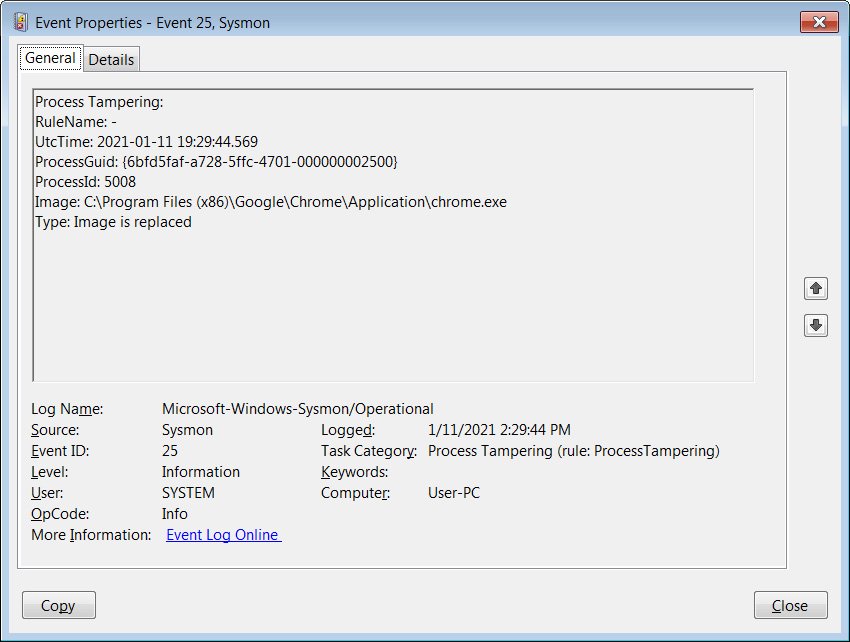
When this feature is enabled then all the process that tries to evade the security is detected and sysmon will generate an event named as “Event-25-Process” that stores all the entry of files.
For more clarification we also attached an image below;

Whereas the experts notice many detections related to these harmless files while executing this code to Firefox, Chrome, Opera, Fiddler, Microsoft Edge, and among the various steps while testing this feature.
Now, the question comes to your mind about what is Sysmon and about its capabilities to know about this in detail then read the coming section.
What is Sysmon?

Sysmon stands for system monitor it is a Windows system service that once installed in the system and then it provides detailed information about the whole process of creation, network connections, and many more things. It will store all the logs generated and help you to identify the malicious or unauthorized activities working on your network.
Capabilities of Sysmon
System monitor has the following capabilities;
- It creates Logs will full command of both current and parent processes
- Records all the hash of process files and images using SHA1, MD5, SHA256
- It also includes process GUID and session GUID logs reports
- Automatically detect changes that happened while creating a file
- Rule the filtering to include or exclude certain events
These are some capabilities that Sysmon offers many more are left.
Summering Up
Sysmon or System monitor tool is strongly recommended to avoid unauthorized access and users can also get the information about multiple things by checking the logs generated by the Sysmon tool.



