Attackers are now using a new ransomware attack named DEARCRY that hacks the Microsoft Exchange servers and was recently used in the ProxyLogon attack.
However, Microsoft also revealed that the attackers were compromising the Microsoft Exchange servers using the ProxyLogon zero-day vulnerabilities, which is the concern of hackers while deploying the ransomware attack.
But, somehow the hackers are misusing the vulnerabilities and executing the DEARCRY ransomware attack.
What is DEARCRY Ransomware?
According to the experts, the DEARCRY ransomware is activated on 9th March and it starts encrypting the files on the system and submitting the ransomware note to the users.
Multiple users started submitting the ransom note and their corrupted file, after proper reviewing the Experts say that most of the users are from Microsoft Exchange Servers.
Whereas, infected users also created a forum topic that states that the Microsoft Exchange server is compromised with the help of ProxyLogon vulnerabilities, and the DEARCRY ransomware is deployed.
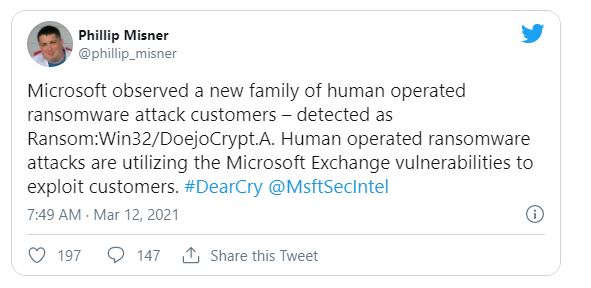
Once this forum gets published that Microsoft also confirmed that the DEARCRY ransomware is executed in human-operated attacks that targeted Microsoft Exchange servers with the help of ProxyLogon vulnerabilities present in the system.
Experts are also able to find out 3 samples of ransomware on VirusTotal [1,2,3] and to all the things which are MingW-compiled and executable. The experts also share the path after analyzing it properly;
C:\Users\john\Documents\Visual Studio 2008\Projects\EncryptFile -svcV2\Release\EncryptFile.exe.pdb
Whereas several experts also think that the DearCry ransomware will try to shut down the Windows services named as ms update. The service is not from legitimate Windows services, but it plays a major role.
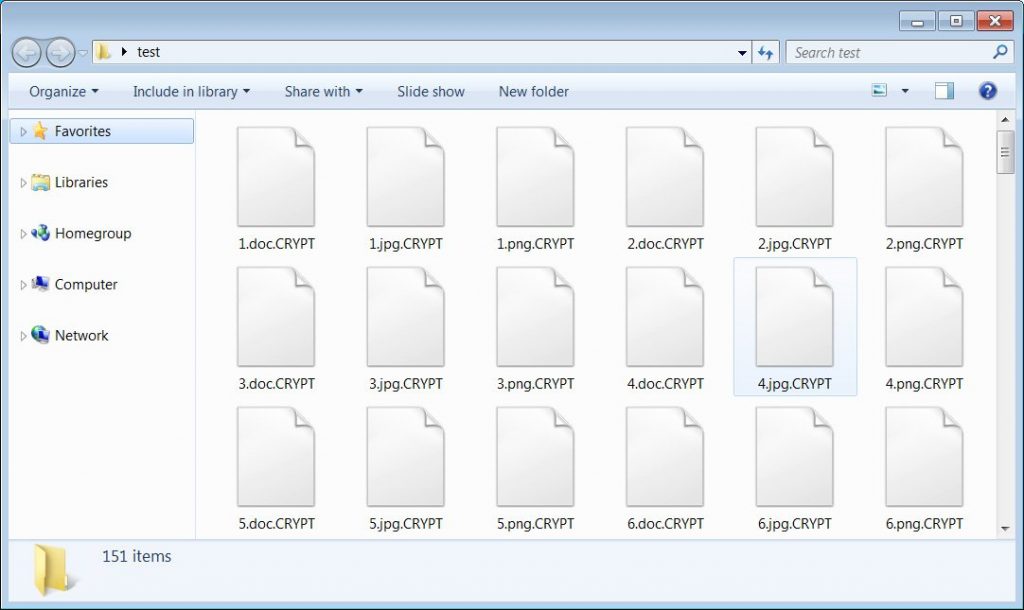
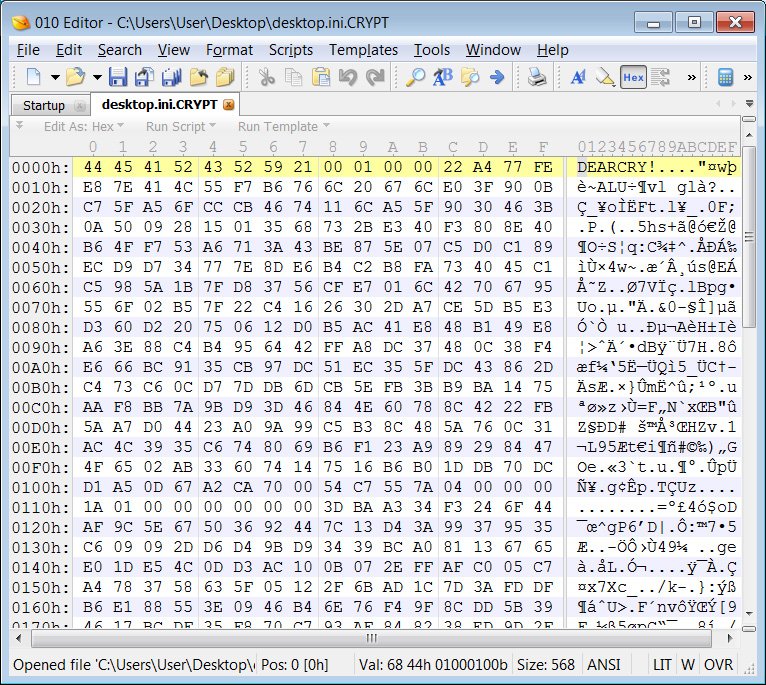
As the ransomware is executed, it will start encrypting the files on the computer and will show the encrypted files with the extension of.CRYPT showed below.
The experts also said that this ransomware also uses AES-256 + RSA-2048 while encrypting the file and executes the DEARCRY ransomware to encrypt all the files.
Once the malware finished the encryption, the ransomware will automatically create a simple ransom note that was named ‘readme.txt’ on the Windows desktop. This ransom note stores two email addresses that belong to the attacker and a unique hash code which is probably of the MD4 hash.
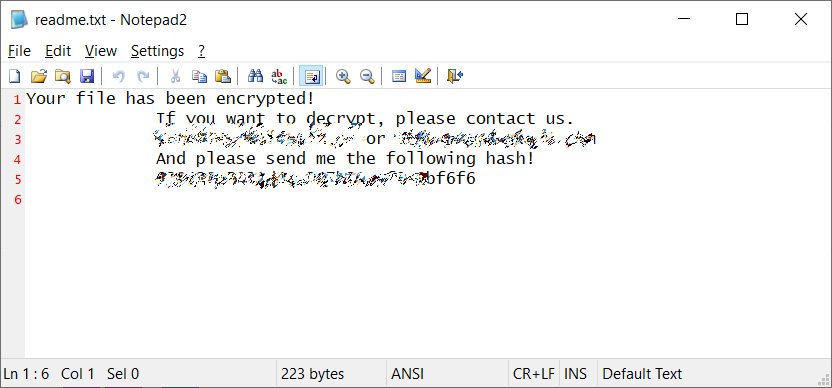
The attackers demand $16,000 for each victim and after the investigation, the experts were unable to find any weakness that helps the victims while recovering their files for free.
What is the Resolution?
Well the ransomware DEARCRY is not confirmed that it is installed in Microsoft Exchange using the ProxyLogon vulnerabilities, there is the chance that it is based on the information at the hand.
According to the data shared by the security firm that thousands of Microsoft Exchange servers are already patched in 3 days and they are working to reduce the effect of this attack.
The organization also said that there are more than 80,000 servers that are not patched directly by applying the updates.
Whereas the Chief Technology Officer of Cortex Networks states that ‘I had never seen any security patch that rated this much high, and widely spreading on Exchange server. Multiple organizations are still running the unpatched version of Exchange and they were been compromised before they apply the new updated patched into their systems, because the attackers are aware about this vulnerbilites present in the server and it may last for 2 months before the Microsoft releases a proper updated and secured patch’
Summering Up
All the organizations are recommended to apply the new patch as soon as possible because this update will not only protect their mailboxes, it will also prevent unauthorized access and prevent your files from encryption.



