According to the investigation, the SolarWinds Orion Network attack must be connected to the Chinese threat Group. Experts from cybersecurity firms report that the attackers are known as Spiral.
Whereas, if we look out towards the attack executed on Microsoft on December 22, 2020, Microsoft said that another group may infect the infrastructure of Orion software which is later named Supernova. However, several security firms find out that both the attack Supernova and Microsoft attack use .NET web shell module is known as “app_web_logoimagehandler” used in the SolarWinds Orion attack.
What Happened Exactly?
The alternation driven by the experts made possible that the SolarWinds application update infrastructure is not breached by anyone, whereas hackers may use unauthorized vulnerability present in Orion API which is further tracked as CVE-2020-10148. This vulnerability permits the attackers to execute unauthorized API commands.
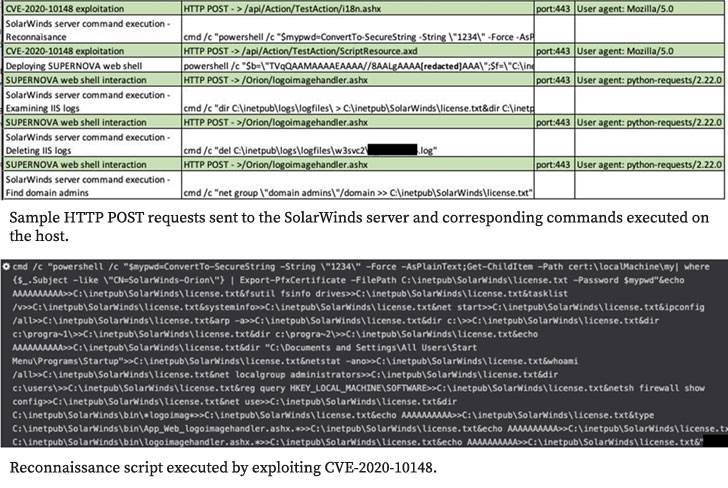
Microsoft also said that unlike the Sunburst attack, the hackers used a malicious DLL file that doesn’t have a valid digital signature which results that this attack is not related to supply chain compromise.
However, multiple experts also claimed that the starting investigation shows that, the attack was linked to Russia and the origin of another attack named Supernova is still a mystery.
What Experts Says?
According to the researchers, who identified the malware in November 2020 while verifying it with their own customer’s network, the urgent way to target the movement that relates this entire attack to Spiral that had the prior knowledge of the framework used in this attack.
As the investigation grows, the organizations also said they found some connections between the attacks that happened and the other attack that was investigated in August 2020, which had been conducted by the unknown group to ManageEngine ServiceDesk in 2018.
Other organizations were unable to catch the attribute of the August attack by the researchers who said that the similarities are founded in Spiral intrusion attack and the Spiral Group is responsible for both the attacks happened.
Conclusion
Since the connection of China will show the fact that the attacks targeting Manage Engine servers are associated with the threat groups that were located in the country and they are unable to mention the modus operandi that exploits long-term persistence and store user data, plunder intellectual data, and exfiltrate sensitive data.
After some time, the solid evidence is captured in the form of IP address the are from China, the researchers also said that this IP address is used by the hackers to run the Securework’s endpoint detection and response software that is used by the hackers. The software used is may be stolen by the system of an infected user.
The Hackers download the endpoint agent from the network and execute it on the attacker that modified the infrastructure. The captured IP address was used unintentionally therefore its geolocation deals with the hypothesis that had been used by the Spiral group the operates from China.



