Lookout security team founded two Android Spying applications that include Hornbill and SunBird. Whereas experts believe that these tools are used by the APT group, which is already responsible for the 2013 state-sponsored attack that targets victims from Pakistan and South Asia.
This group identified was previously reported in 2017 as they are executing the mobile malware and Android surveillance using ChatSpy. This discovery of Hornbill and SunBird shows that the group is active and started spying on mobile users for the year before they execute ChatSpy.
These attackers target Pakistan’s military, Indian election authorities in Kashmir, and nuclear authorities. These two malware identified to have the capabilities to execute SMS, encrypted messaging application content and geolocation, and other confidential information.
SunBird malware has the following capabilities listed below;
- The Application uses specific locations in Kashmir or Falconry Connect and Mania Soccer.
- This app also deals with Islam-related application that includes Quran Majeed
- Offers security services like Google Security Framework.
Lookout the agency who discovered this attack named Hornbill after Indian Grey Hornbill, which is also known as the state bird of city Chandigarh and where these developers of Hornbill are situated. Whereas SunBird is named from the services that contain malware called as SunService, it is also from native India.
Now, in the upcoming section read the functionality and impact of both the SunBird and Hornbill.
Functionality of SunBird and Hornbill
These two malware have some similarities and differences as the way depends on their execution on the victim’s devices. SunBird has the facility of Remote Access Trojan which tends to execute the remote commands on the victim’s device by the attacker. Whereas Hornbill is a surveillance tool that is used to steal a selected set of information that the attacker needed.
SunBird and Hornbill Both are capable to extract a wide range of data that includes; Contacts, Call logs, Geolocation, WhatsApp notes, Device metadata that deals with phone numbers, IMEI ID, Manufacturer, and Android version.
Both the malware are also capable to execute the following action on the infected devices that deal with;
- Storing victims current screen, Capturing screenshots
- Request device admin privileges
- Record call audio and environment
- Take photos from the device camera
- Steals WhatsApp notifications and other services
- Capture WhatsApp messages and accessibility services
Now read the upcoming section to know about the specific functions of this malware.
Hornbill Functionality
This is a more sophisticated tool as compare to SunBird. It is not used to target the victim’s data, the malware has the capabilities to uploads the data when it runs. Once the data is uploaded it will keep the mobile data and battery usage low. The entire uploads started when data is monitored by Hornbill changes that deal with SMS, WhatsApp notifications are received from calls made from the devices.
The malware works in the victim’s device and they closely monitor the resources. For example, if your device storage is low that it triggers the garbage collectors and while adding the extra data is use the hardware information.
Information stored by Hornbill is hidden in a hidden folder located on the internal storage and once the data is uploaded through Command and Control server it will delete the data from the device. Hornbill only records the logs that the attacker needed. It also uses the different set of the server that communicates with C2 and the server path that Hornbill uses is described below.
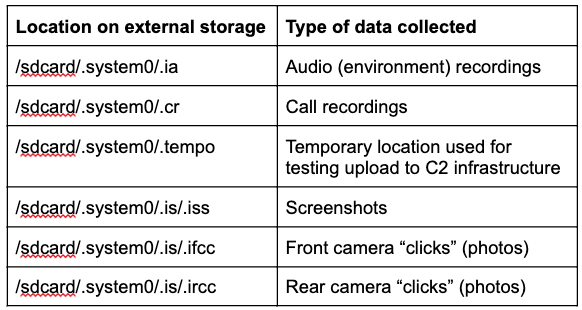
The attacker behind the Hornbill is very much interested in the user’s communication and the message content along with the sender information. Hornbill stores the WhatsApp calls and activated calls by manipulating the Android’s services. The entire exploitation is work in the manner to observe the Android’s surveillance.
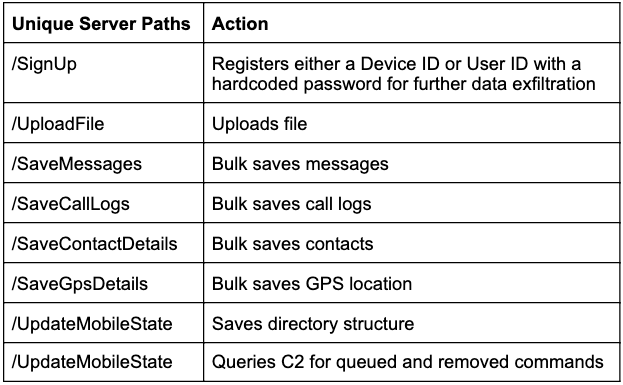
At last, Hornbill monitored the activity on the document stored on external storage that includes the file having an extension of .doc, .pdf, .docs, .ppt, .xlsx, .txt, and others whenever the documents are created, modified, closed, opened, deleted, or moved. The action is logged by Hornbill and it also modified the list of suffixes, the latest samples of Hornbill displays that the malware is under development and is updated day by day.
Now read the upcoming section to know about the Sun-Bird Functionality in detail.
Sun-Bird Functionality
It is the critical malware that has a unique set of capabilities as compared to Hornbill. It uploaded the data into regular intervals using command and control servers. The information is collected in an SQL database and then compressed into ZIP files. The Sun-Bird is capable to extract the data that consists of the following details.
- List of Installed Application on the Device
- Calendar Information
- Browser History
- WhatsApp documents, databases, voice notes, audio files, and many more
- Data sent and received through IMO and other messaging application
- It is also capable to download specific content from FTP servers
- Run arbitrary commands as root
- BlackBerry Messenger BBM audio files, documents, and images
- Scrape BBM notifications and other services

What Happened Next?
Lookout’s discovered the latest samples by Hornbill in December 2020 and they still think the malware is activated. Both the Hornbill and ChatSpy packaging dates are tampered with and observed in January 2018 and May 2018.
The organization observed the SunBird in January 2017 and the other two malware between December 2016 and in early 2019.

Hornbill is identified in May 2018 and it is actively executing and the company also find out the new samples in early 2017 and in late December 2019.
Who is Targeted?
SunBird was deployed over 18GB of exfiltrated data that was publicly exposed using 6 different Command and Control servers and after that, all the data is uploaded to C2 infrastructure that includes the details of infected devices.
This information is attached with the data content and gave results about the users who are targeted by this malware and what kind of information is leaked by the attackers.
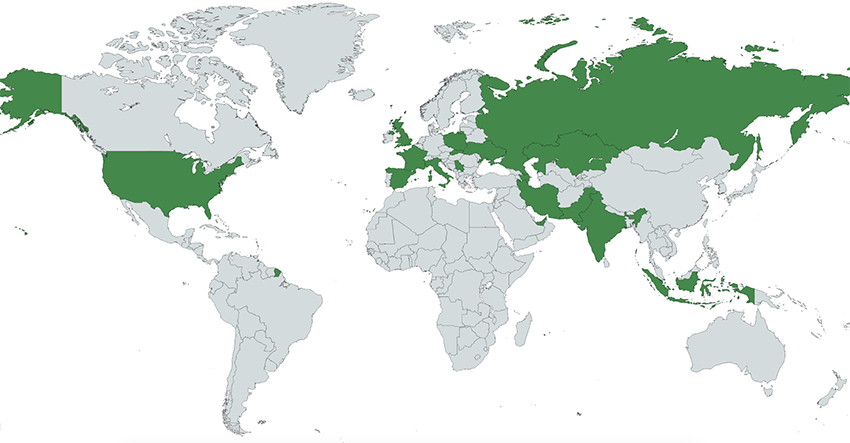
Some targets are from the Pakistan Atomic Energy Commission that includes multiple contacts in Pakistan Air Force officers and others who are from the electoral rolls department situated in Pulwama district of Kashmir.
Malware Development and Commercial Roots
This malware is getting evolved day by day and used Android surveillance tools. Hornbill is derived from the same code based on a previous application named as MobileSpy. It is still unclear that how the developers of Hornbill take the code and but the organization working behind included MobileSpy, Retina-X Studio, and shut the surveillance in 2018 May.
Links between these Hornbill developers show that they all are working together in Android as well as in iOS development organizations.
SunBird is created by Indian developers who also created several other spyware applications which are named as BuzzOut. The SunBird roots are lay on stalker were and were supported by the content discovered in exfiltrated data. The entire data contained the information of stakerware victims located in Pakistan and traveling from UAE to India.
Role of Exfiltrated Data
According to the Investigation, the exfiltrated data of SunBird whose command and control servers are secured.

This breakdown described in an image is the type of SunBird exfiltrated data and this is from the content exposed and other 5 campaigns between 2018 and 2019. The experts found other 12 GB of data that are exfiltrated on another C2 server named 23.82.19[.]250. The language used in the server was set up as Chinese and this is a false flag or may be altered by a third-party.
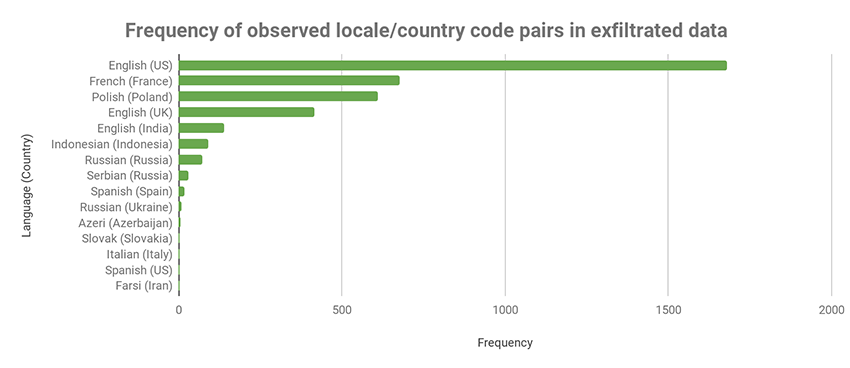
The frequency of infected devices is located with the county code and packaged with public accessible extrafilterated data and it also includes both the Confucius APT targets and other spouse are victims of SunBird.
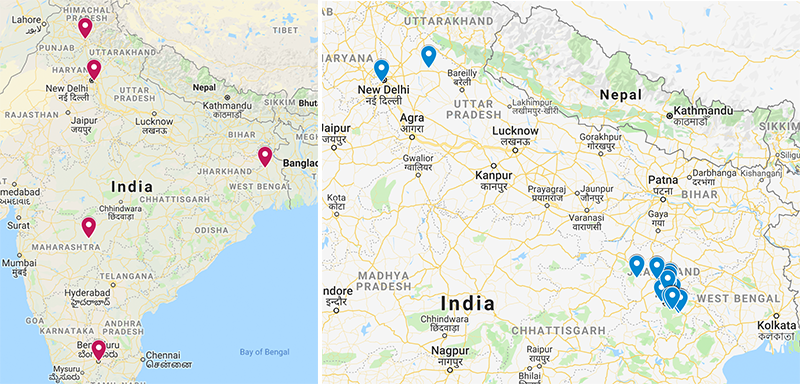
Other Connection
Other previous tactics are seen with ChatSpy Hornbill samples and applications are Fruit Chat, Cucu Chat, Kako Chat, and other related C2 infrastructure that communicates on port 8080. The Pakistan Federal Bureau of Revenue published other data.
Summering Up
All the information in the reports is based on the research and analysis by the experts. The belief the information is provided has no liability. Users need to aware of the ongoing operations and these types of updated and sophisticated malware attacks.



