It is all started with the code of SolarWinds.Orion.Core.BusineddLayer.dll While examining the effects of SolarWinds Orion’s supply-chain attack, the agencies discovered another backdoor.
This newly uncovered backdoor is different from Sunburst called SUPERNOVA. The vulnerability present in SolarWinds Orion Software addresses another zero-day to deploy SUPERNOVA malware in users’ environments.
According to agencies that supply chain attack on SolarWind’s Orion software is now turning on a high degree of technical sophistication and compromises approx 18000 + SolarWinds customers. Drive through to the forthcoming section to know about the new backdoor in detail.

What is SUPERNOVA?
This SUPERNOVA malware is plated as a web shell in the code of SolarWinds network that facilitates to run of the arbitrary code that installed the trojanized version of the software in target environments.
SUPERNOVA is a conventional web sell attack that is often some interactive frontend document that can be manipulated easily to process backend side effects which are also working as remote code execution (RCE). A web shell is designed in such a way that it might be uploaded, downloaded, or deployed by targeting the vulnerability present in the server.
A web shell is a malware that is embedded in a page and implemented in a programming language like PHP, Java, JSP, C#, ASP.NET, etc. along with that it receives commands from the remote server and executes in a web server under the runtime environment.
According to the CERT coordination center, the SolarWinds Orion API which is as an interface with all other Orion systems now suffers from a security flaw (CVE-2020-10148) that permits the attacker to execute unauthorized commands.
This web shell is a malicious version of an affected .NET library present in Orion software from SolarWinds, constructed in a way that it bypasses the automatic defense mechanisms. The attacker has assembled a stealthy .NET API along in Orion binary and it allows the attacker to deploy full-featured .NET code in-network or in other attack phases.
Working of SUPERNOVA
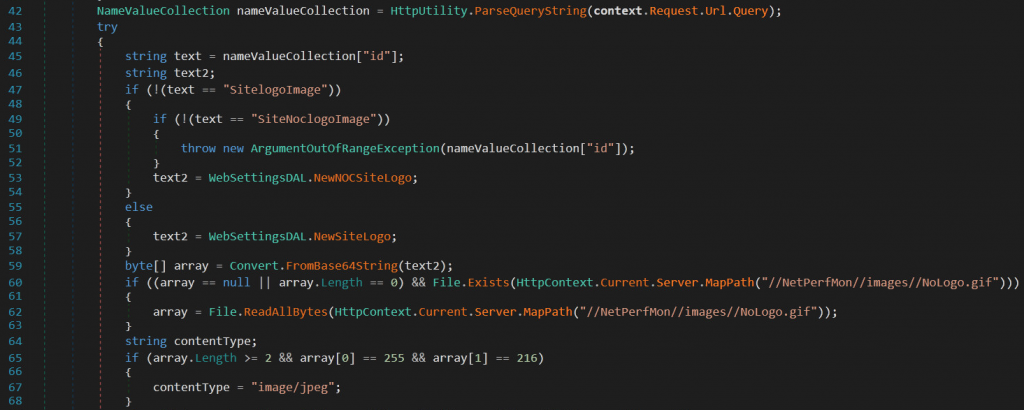
This is the trojanized copy of app_web_logoimagehandler.ashx.dll which is part of SolarWinds .NET that works over an HTTP API.
According to the specialist, the actor sends the request to the embedded webshell through the internet. The code is designed to accept the parameters as the part of the .NET program, that was compiled inside the memory.
Along with that the experts also say that there are so many commands that executed to prevent the operator error causing an unhandled exception in Orion and trigger unwanted scrutiny. This enter procedure is also known as dynamic code execution which parties the program to be flexible or more extensible.
The SUPERNOVA manages the webshell attributes to other web shells and secretly plant the malware onto the server then it receives the C2 signals remotely and executes them which makes it more sophisticated because of its in-memory execution.
Also, it is not cleared that how long SUPERNOVA is been active but according to malware analysis, it displays the timestamp of March 24th, 2020.
Who is Behind This?
Based on the findings and investigations the SUPERNOVA is operated by the advanced hacking group that ultimately wants to compromise with the help of webshell to a new level. The experts also said by adding a .NET program in memory execution makes SUPERNOVA is a tough enemy.
Whereas Microsoft says that “SUPERNOVA is the interesting turn of events, the entire investigation of SolarWinds attack compromises leds to the discovery of this additional malware that effects the SolarWinds Orion product and was operated by the different threat actor”
Another agency says that SUPERNOVA doesn’t have any digital signature and initially it is discovered in SolarWinds SunBurst malware attack.
Precluding and Benchmarks
According to SolarWinds Security Advisory user should have to update the relevant version of SolarWinds Orion Platform:
• 2019.4 HF 6 (released December 14, 2020)
• 2020.2.1 HF 2 (released December 15, 2020)
• 2019.2 SUPERNOVA Patch (released December 23, 2020)
• 2018.4 SUPERNOVA Patch (released December 23, 2020)
• 2018.2 SUPERNOVA Patch (released December 23, 2020)
Customers who already updated don’t need to worry about both the SUNBURST and SUPERNOVA backdoor and no further action is required.



