On 10th March 2021, the cybersecurity researcher said that they founded a complicated backdoor that targets the Linux servers and endpoints and they also believed that it was the work of Chinese Hackers.
How do the Experts Know?
According to the investigation, the backdoor is similar to the malware that was used in the previous attack that is associated with the Winnti Umbrella hackers group which includes PWNLNX, XOR.DDOS and Groundhog.
Whereas the name RedXOR’s comes from the fact that used to encode the data that is based on XOR and it has also complied with a legacy GCC compiler that releases Red Hat Enterprise Linux, and the malware is capable while deploying the targeted attack to the selected Linux Systems.
The experts display two examples of malware that were used between Indonesia and Taiwan, both countries blamed China for this attack that happened on 23-24th February.
However, the attacks also bypass the terms of overall flow and functions, they also use XOR encoding between the RedXOR and PWNLNX. The backdoor will take the form of an unstripped 64-bit ELF file completed with the typosqatted name that deals with po1kitd and polkitd. Once these files get executed it will create a hidden directory and store all the files that malware needed before executing into the victim’s machine.
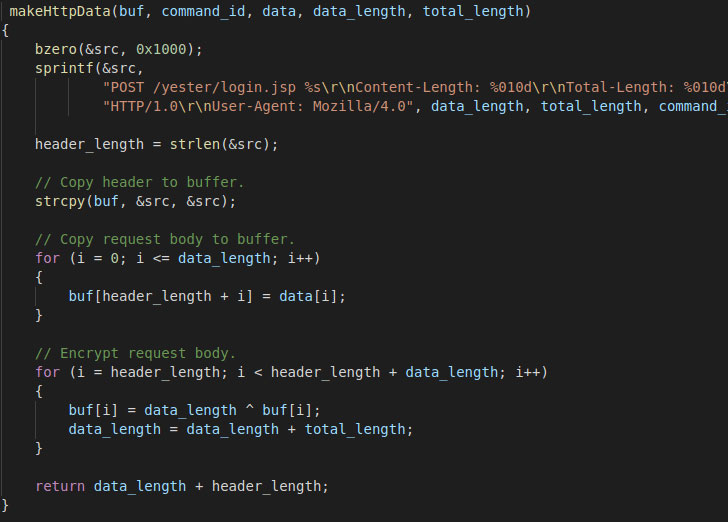
Polkit is the toolkit that is used for handling the authorizations and also for all the unprivileged processes that connect with privileged processes.
This malware also comes with the encrypted configuration that uses the command-and-control IP address and port and the passwords that need to be verified by the C2 server before starting the TCP socket.
The communications are not disrupted with HTTP traffic, it is also encoded with both the ways used in XOR encryption that results in decrypted data that needs a command to run.
Since the RedXOR deals with multiple capabilities which include gathering the system information that holds the username, MAC address, clock speed, kernel version, distribution, etc. and it is also capable to perform commands like operations, running the arbitrary shell commands, executing the system privileges and also it gets updated the malware remotely.
Summering Up
Users who are infected with RedXOR have to take the protective measures used for killing the process and removing all the files that are used by the malware.
However, the latest development points also increase the number of activated attacks that are now targeted the Linux systems and are part of the widespread adoption that an OS had. It also deals with IoT devices, web servers, cloud servers and assisting the hackers to initiate the port of their existing Windows tools that are used in Linux or they can also develop new tools that support both the platforms, this will increase the following the attack.
Whereas some nation-state attackers are also incorporating offensive Linux features into their attack and it is also expected that these attacks are increasing in the upcoming days and they were getting more complicated and sophisticated than the earlier ones.



