SAP released another security update for this month that identified multiple sophisticated vulnerabilities in which most complicated vulnerabilities are rated as highest severy score that also infects the company client products.
The other two vulnerabilities that the organizations had got the patches and in these vulnerabilities the unauthorized users get the configuration data and initiate remote code execution.
However, on Tuesday the SAP security team released the information about these bugs that were identified and fixed in the recent update. According to the SAP, there is 19 security bug and five of them are list as old vulnerabilities.
Which Vulnerabilities are Fixed by SAP?
These updates will be fixed all the vulnerabilities which may impact the SAP business clients and the user interface that works as an entry point with other SAP business applications. The security did not resides in the product or in browser control that comes along with it. The organization had not aware of these vulnerabilities they only rated it as with 10 out of 10 maximum severity score.
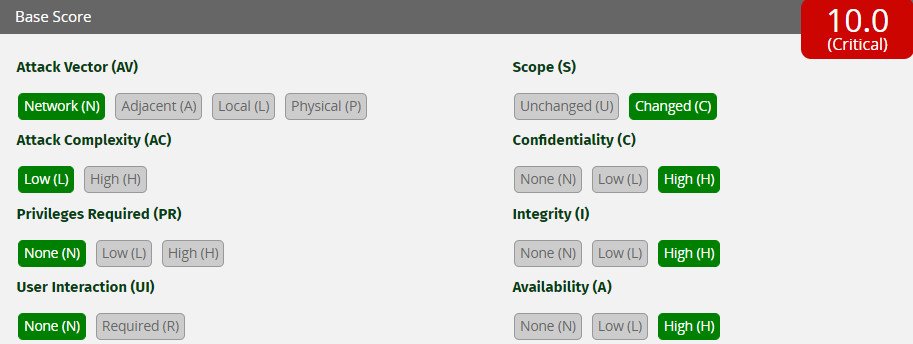
Whereas, the organization delivered an updated that fixed all the remote code execution bugs present in SAP Commerce that was used to create the product information and migration of the data through different communication channels.
The vulnerabilities that affect the SAP Commerce version are included 1808, 1811, 1905, 2005, and 2011 are identified as CVE-2021-27602. SAP also identified these bugs as critical and gives 9.8 out of 10. Whereas, the National Institute of Standards and Technology is still investigating it and may re-write the lower severity score.
Meanwhile, the attacker authorized the Backoffice Product Content Management application of SAP Commerce as an exploit while gaining the remote code execution on the system and injecting the malicious code into the source rules.
After the previous update, the organization reviews the critical bugs that deal with Migration Service components in the NetWeaver software stack that affects the versions 7.10, 7.11, 7.30, 7.31, 7.40, 7.50 which permits the organizations to integrate the data and business process of multiple sources.
However, the vulnerability tracked as CVE-2021-21481 and the SAP list is having a score of 9.6 out of 10 but the NIST gives it a base score of 8.8 out of 10.
Conclusion
All the bugs addressed by the update in the Migration Services did not execute the authentication check and the unauthorized attacks will access the configuration data while misusing the administrative rights on the system. The other fixes the SAP that delivered the security patch over the bugs that was covered in the company having the high severity score are described below;
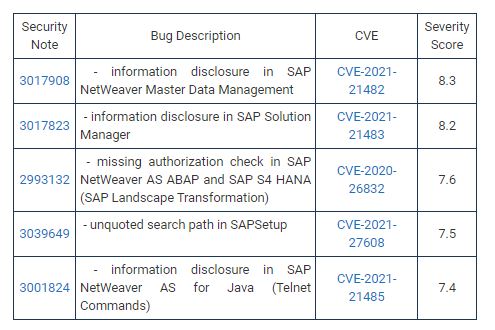
The organization released the patch for all the medium scored vulnerabilities ad the organization also said that multiple bugs that affect the same product can be covered in one security note.



