The number of malicious dormant domains is on the rise, and as investigators alert, approximately aged domains pose some form of danger. This was an awareness that hit the investigators when it was disclosed that the threat actor relied on domains registered years before their malicious activities began.
According to that, efforts in analyzing the critically elderly domains before they get the chance to start the attacks and support malicious activities have picked up the pace. A report from our security researchers disclosed their investigators’ researches after looking at tens of thousands of domains each day in whole September 2021.
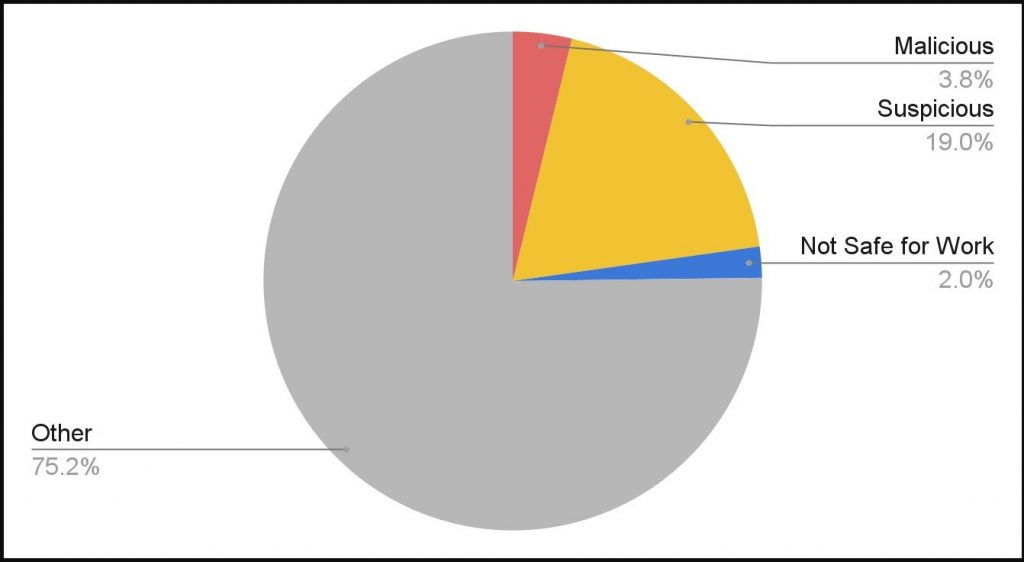
They come to the point that around 3.8% are straight-out malicious, 19% are suspicious, and 2% are unsafe for work environments.
Why Permit a Domain Age?
The main aim behind registering a domain long before the attacker will utilize it is to design a “clean record” that will avoid security detection systems from undermining the success of malicious campaigns. Typically, advance registered domains (NRDs) are more likely to be malicious, so the security solutions treat them as suspicious and have more chances to flag them.
However, Unit42 explains in its report that strategically aged domains are three times more likely to be malicious than NRDs. In some cases, these domains stayed dormant for two years before their DNS traffic suddenly increased by 165 times, indicating the launch of an attack.
What are the Symbols of “snake eggs”?
An obvious sign of a malicious domain is the sudden spike in its traffic. Appropriate services that registered their domains and launched services months or years later exhibit gradual traffic growth. The domains that weren’t destined for legitimate use generally have incomplete, cloned, or generally questionable content. As expected, WHOIS registrant details are missing too.
The other clear symbol of a purposefully aged domain that is meant to be utilized in malicious operations is DGA subdomain generation. Domain Generation Algorithm (DGA) is an established method of creating different domain names and IP addresses to serve as advanced C2 communication points. The goal is to avoid detections and blacklists. By looking at the DGA element alone, Palo Alto’s detectors identified two suspicious domains each day, spawning hundreds of thousands of subdomains on the day of its activation.
A Realistic Example
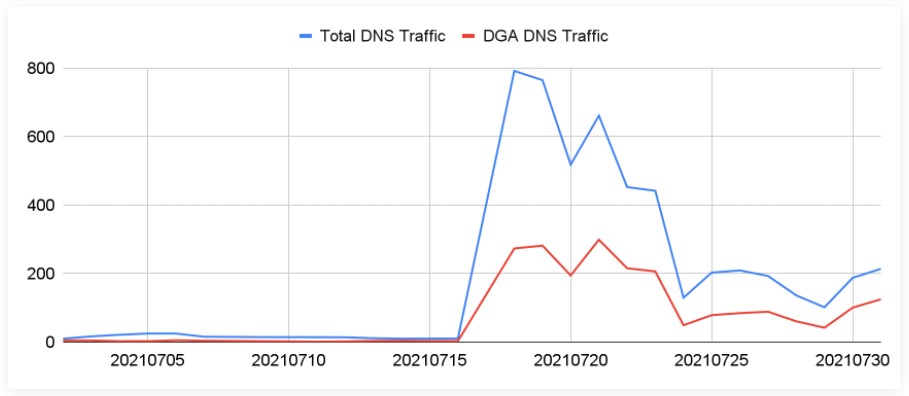
One notable case captured by Unit42 in September was a Pegasus spying campaign that used two C2 domains registered in 2019 and awoke in July 2021. DGA domains played a vital role in that campaign, carrying 23.22% of the traffic on the activation day, which spiked 56 times higher than normal DNS traffic volumes. A few days later, DGA traffic reached 42.04% of the total.
Other real-world examples detected by the researchers include phishing campaigns that used DGA subdomains as cloaking layers that will direct ineligible visitors and crawlers to legitimate sites while pushing victims to the phishing pages.
This shows that these DGAs serve not only as C2 domains but also as proxy layers that can be explicitly configured to the campaign’s needs. Finally, there were also cases of wildcard DNS abuse, with multiple subdomains all pointing to the same IP address.
“These hostnames serve randomly generated websites that fill out some website templates with random strings,” details the security researcher’s report. “They could be used for black hat SEO. Specifically, these web pages link to each other to obtain a high rank from search engine crawlers without providing valuable information.”
In most cases, strategically aged territories are used by cultivated actors who perform in a more organized context and have long-term plans. They’re used for leveraging DGA to exfiltrate data through DNS traffic, serve as proxy layers, or mimic the domains of well-known brands (cybersquatting). Although noticing DGA activity is still inquiring, defenders can achieve a lot by monitoring DNS data like queries, responses, and IP addresses and focusing on recognizing patterns.



