A Russian national trusted to be a member of the TrickBot malware development team has been abandoned to the U.S. and is actively facing what could get him 60 years in prison. 38-years old Vladimir Dunaev, also known as FFX, was a malware developer that managed the creation of TrickBot’s browser insertion module, the indictment alleges.
He is the second malware developer associated with the TrickBot group that the Department of Justice arrested this year. In February, Latvian national Alla Witte, also known as Max, was arrested for writing code related to the control and the set up of the ransomware.
Who are the Older Members of the Gang?
Dunaev was arrested in South Korea in September as he was trying to leave the country. He had been forced to stay there for more than a year due to Covid-19 travel restrictions and his passport expired. The surrender was complete on October 20.
He is believed to have been involved with the TrickBot group since mid-2016 by pursuing a recruitment test that involved creating an application that assumed a SOCKS server and notifying a copy of the Firefox browser.
He passed both tests with flying colors, showing skills that the TrickBot group required. “He’s capable of everything. Such a person is required,” comes from the conversation between two members of the group responsible for recruiting developers.
Starting June 2016, the defendants created, modified, and updated codes for the TrickBot malware gang, the allegations allege.
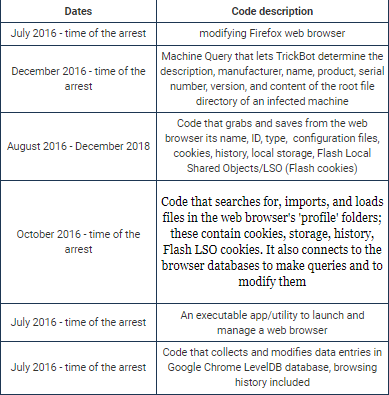
Between October 19, 2017, and March 3, 2018, members of the TrickBot group that included Dunaev and Witte successfully wired more than $1.3 million from the victim’s bank account.
A large, well-organized group
According to the indictment, the TrickBot gang has at least 17 members, each with specific attributes within the operation:
- Malware Manager – who outlines the programming needs, manages finances, deploys TrickBot
- Malware Developer – who develops TrickBot modules and hands them to others to encrypt
- Crypter – who encrypt the TrickBot modules so that they evade antivirus detection
- Spammer – who use distribute TrickBot through spam and phishing campaigns
Created from the ashes of the Dyre banking trojan in 2015, TrickBot focused on stealing banking credentials initially, via web injection and logging the victim user’s keystrokes.
Later, it developed into modular malware that could also distribute other threats. These days, the gang has a preference for dropping ransomware on company networks, Conti in particular.
TrickBot is believed to have infected millions of computers, enabling its operators to steal personal and sensitive information (logins, credit cards, emails, passwords, dates of birth, SSNs, addresses) and steal funds from victims’ banking accounts.
The malware has impacted businesses in the United States, United Kingdom, Australia, Belgium, Canada, Germany, India, Italy, Mexico, Spain, and Russia.
Apart from Dunaev and Witta, the DoJ has indicted other members of the TrickBot gang whose names have not been revealed and are located in various countries, Russia, Belarus, and Ukraine.
Dunaev is currently facing multiple counts of complicated identity theft, wire fraud, bank fraud. As well as conspiracy to commit computer fraud, aggravated identity theft, and money laundering. All the charges against him come with a maximum penalty of 60 years in federal prison.



