All the Windows users, here’s the news for you: a new vulnerability has been detected across various versions of the PC operating system that could permit serious exploits, like remote attackers gaining access to the computer and customizing your personal information.
Named “PrintNightmare,” the exploits take benefits of this security vulnerability discovered with the Windows Print Spooler service. Despite the need for authentication, the security of the issues is sensitive as threat actors can use it to make over a Windows domain server to easily set up malware across a company’s network.
When it was First Discovered?
It’s a bit complicated to know what exactly has happened but starting from early June, as part of the routine Patch Tuesday process, Microsoft discovered a patch known as CVE-2021-1675 for what they termed as a “low severity” privilege-escalation vulnerability in Windows Print Spooler.
After some days, on 21 June, Microsoft again classifies the security patch as “critical”, explaining it as a more deliberate “remote code execution” vulnerability. The patch affects Windows Print Spooler and because of the wide list of errors impacting this component over the years. Some researchers have examined the leaked PoC exploit on fully patched Windows Server 2019 systems and were allowed to execute code as SYSTEM.
How did the Accidental Leak Happen?
The leakage of the details for this vulnerability was accidental, as it was mistakenly for another issue, CVE-2021-1675, which also affected the print spooler that Microsoft patched in the previous month’s security update release.
As above mentioned, Microsoft revealed CVE-2021-1675 as a high-severity, privilege escalation issue but a couple of weeks later change the rating to critical and the impact of Remote Control Execution, without providing any details.
Considered for reporting CVE-2021-1675 are researchers from all of these three cybersecurity companies i.e. Tencent, AFINE, NSFOCUS but different teams were examining Windows Print Spooler.
On 28th June, Chinese security vendor QiAnXin revealed that they discover a way to exploit the vulnerability to gain both the local privilege escalation and remote code execution and also posted a demo video.
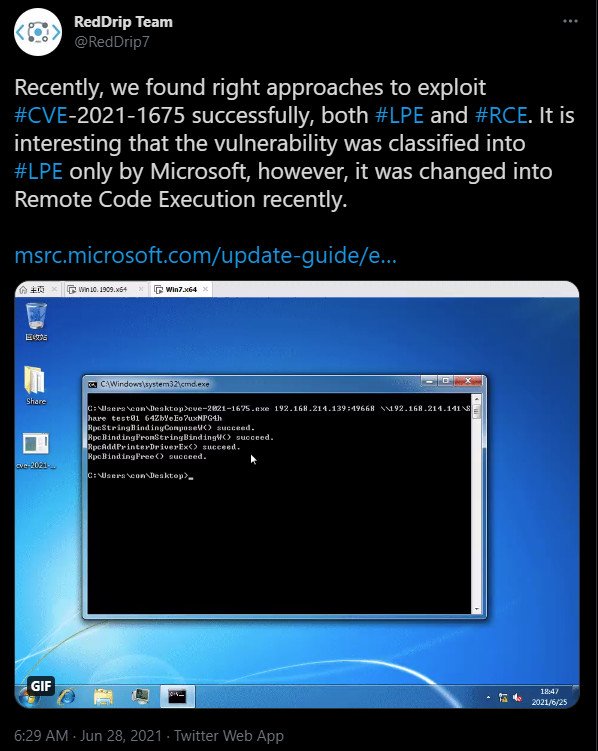
While seeing the exploit video, another team of researchers from Chinese security company Sangfor, decided to post their technical write-ups and a demo exploit for remote code execution (RCE), naming the bug PrintNightmare.
It changes out that Microsoft’s patch for CVE-2021-1675 on June 8 was incomplete and the PrintNightmare RCE exploit works on up-to-date systems.
What Experts are Doing?
Without any information from Microsoft about the issue, the vulnerability generated confusion among security researchers, some of them accepting that PrintNightmare was an isolated, zero-day error that required its recognition.
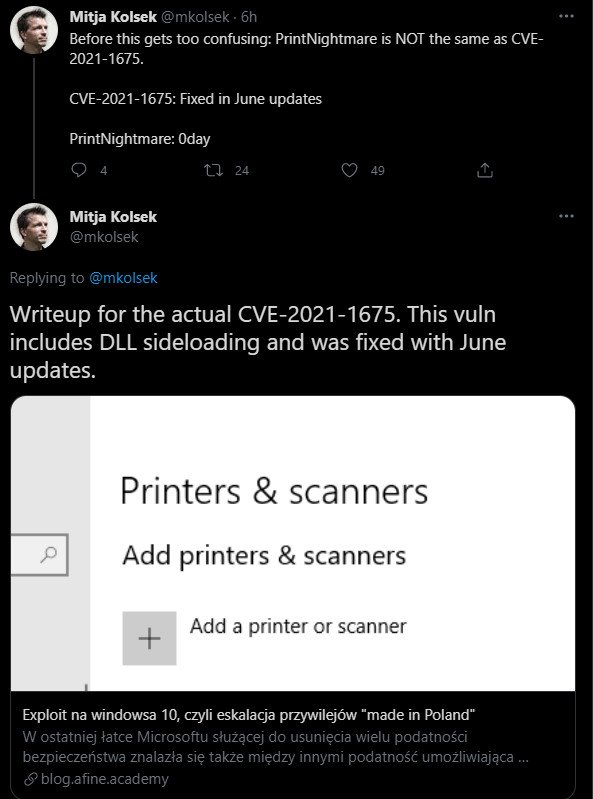
CEO of Across Security Mitja Kolsek and the co-founder of micro patching services oPatch tested to clear the confusion by pointing to the technical details that AFINE researchers released for CVE-2021-1675.
Through, one of the researchers that described CVE-2021-1675 to Microsoft, Yunhai Zhang of NSFOCUS, explained why the patch does not block the PrintNightmare exploit.
Yunhai Zhang said “CVE-2021-1675 is meant to fix PrintNightmare, but it seems that they just test using the test case in my report, which is more delicate and also more restricted. So, the patch is incomplete.”
Benjamin Delpy, the developer of the mimikatz post-exploitation tool for penetration testing, analyzed things even more by observing that only patched servers promoted to domain controllers are affected.
How to Control this Error?
PrintNightmare is a serious error that requires to be treated accordingly. Since an error is yet to arrive, administrators are actively suggested to stop and disable the spooler service on domain controller systems.
Security consulting company Lares published a repository with discloser and amends data that consist of a sample of the PrintNightmare attack and a Sysmon configuration file for telemetry purposes.
Florian Roth of Nextron Systems generated experimental Sigma rules for analyzing print spooler exploitation based on Sangfor researchers, exploit code.
Lares also gives details on how to stop or disable the spooler service either from the Group Policy settings or by utilizing the PowerShell script. The CERT/CC has also posted a guide on how to stop or disable the print Spooler services.
The co-founder of Hacker House Matthew Hickey was able to acquire full SYSTEM privileges from a normal Domain User account on an up-to-date Windows Server 2019 machine vulnerability to PrintNightmare.
Delpy achieved remote code execution with the highest privileges on a fully patched system. While his assessment was also performed on a domain controller, Delpy said the similar outcome is achieved with the available RPC to the spooler, remote or local.”
Delpy created a video showing that their test systems, showing that his test system, running the latest updates, did not stop the PrintNightmare exploit.
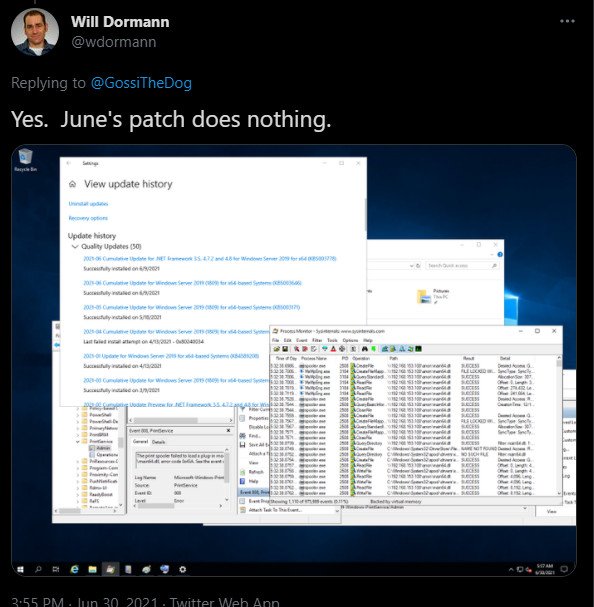
The vulnerability analyst Dorman for CERT/CC confirmed that an authenticated remote threat actor could run inflated code on a computer with the print spooler services enabled.
Dormann also confirmed that Microsoft’s June security updates did not affect the zero-day PrintNightmare vulnerability characterized by Sangfor researchers.
The most common suggestion advice right now is to disable and stop the services on domain controllers as soon as possible, as the requirement for authentication is not an obstacle to an attacker.
Attacker, specifical gangs like ransomware gangs, is likely to grab this opportunity to negotiate corporate networks as it is an easy task to generate the credentials for blocked domain users, security researchers Jonas Lykkegard told our experts.
Passwords for ordinary users can be just as good to the threat actor in environments prone to escalations, and there is a market for all this type of data backed by data theft activities.
There are some of the underground forums, a valid credentials pair for a Window Remote Desktop Server can cost worth $3 and $70, respectively.
One of the biggest Windows Remote Desktop login marketplaces had a collection of about 1.3 million login details, which shows that selling is a profitable business.
Zhiniang Peng, XueFeng Li, and Lewis Lee Sangfor researchers will talk at Black Hat this year about how they discover PrintNightmare and generated an exploit for it in a presentation with the title Dividing Into Spooler: Discovering LPE and RCE vulnerabilities in Window Printer.
Further Updates
Update on June 30, 18:45 EST: Added information about discovering PrintNightmare exploit attempts and disabling the print spooler service to avoid attacks.
Update on July 1: Added comment on PrintNightmare being similar to CVE-2021- 1675 from Yunhai Zhang of NSFOCUS, credited for the discovery and reporting for the vulnerability, and from various penetration tools developer Benjamin Deply.
Update on July 2: Microsoft has given the most needed explanation on PrintNightmare by stating that is it “similar but different from the vulnerability that is authorized CVE-2021-1675” and that it existed before June in 2021 security updates.
Also, PrintNightmare remains in all versions of Windows and was authorized a new identification number, CVE-2021-34527. Microsoft warned its Microsoft 365 Defender users that the vulnerability is currently exploited by threat actors.



