By the Wormable vulnerability in the HTTP Protocol Stack of the Windows IIS server can also be treated to offense unpatched Windows 10 and the Server systems universally disclosing the WinRM (Windows Remote Management) service.
During the May Patch Tuesday Microsoft patched the sensitive error followed as CVE-2021-31166. Fortunately, Using the remote code execution (RCE) attacks it can be victimized by a threat too. The only impacted versions 2004 and 20H2 of Windows 10 and Windows sever by the vulnerability.
Microsoft also suggested prioritizing patching all overwhelmed servers because the vulnerability could permit the unauthorized attackers to implement inconsistent code remotely “in most situations” on vulnerable systems.
Computing to this, at the end of the week, security analyst Axel Souchet has broadcast the demonstration-of-concept exploit code that can be handle to clash unpatched system using mischievous designed packets by activating blue screens of death.
What Error was Erect?
An error was erect in the HTTP Protocol Stack (HTTP.sys) which is used as a protocol listener by the Windows IIS Web Server for functioning HTTP requests.
A Security researcher Jim DeVries also discovered that it probably affects Widows 10 and Server devices accessing the WinRM services know as Windows Remote Management, an element of the Windows Hardware Management functionality set which also enables the use of the vulnerable HTTP.sys.
Whereas Remote users have to allow the WinRM service manually on their Windows 10 computer, operation Windows Server endpoints have WinRM clipped on by default which assembles them endangered to adversary if they are using versions 2004 or 20H2.
Experts say that “[CVE-2021-31166] is most commonly accessed in corporate sectors. It’s accessible by default on the servers”.
“I don’t think that this is a huge risk for remote PCs but should someone marry this virus and ransomware, it could go wild in corporate environment.”
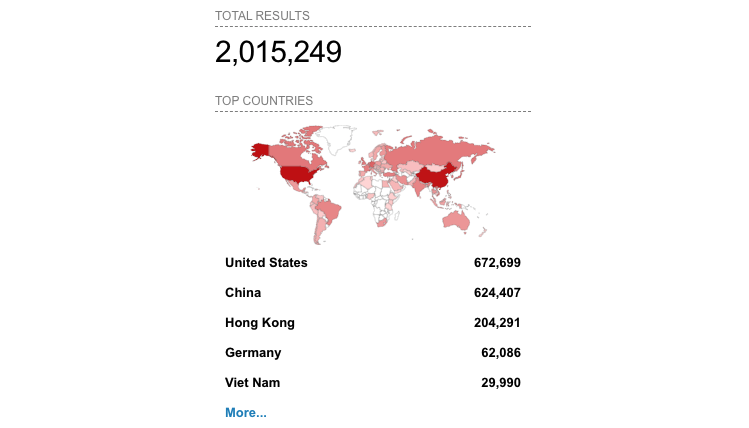
More than 2 Million Internet-discovered WinRM Servers
Our Experts have also been confirmed by CERT/CC unprotected analysis Will Dormann who fortunately crashed a Windows computer discovering the WinRM service using Souchet’s DoS exploit.
Dorman also found that around 2 million Windows computers tracked over the internet are discovering the unprotected WinRM services. Although, barely a subset of all these Internet-exposed Windows computers is vulnerable seems that the vulnerability only affects Windows 10 and Windows Server, versions 2004 and 20H2.
The accomplishment release could permit vulnerabilities to design their exploits quickly, probably also permitting remote code execution.
Whereas, the effect should also be limited and the patching process a bit faster since most remote users running Windows 10 versions have potentially updated their systems last week. Like wisely, many corporations should likely be secure from attacks targeting the error since they don’t frequently set up the latest Windows Server versions as soon as they are released.



