Details related to the security feature overlap the vulnerability present in Windows NT LAN that was displayed that the Microsoft updates are part of this.
This exploit is tracked as CVE-2021-1678 and termed as a remotely exploitable flaw founded in the vulnerable component that was connected to the network stack and exact the details of multiple unknown errors.
Crowstike researcher said that the security bug founded, If remain unpatched could permit the attacker to get the remote code execution thorough NTLM relay.
This entire vulnerability discovered to authorize the hackers to relay on NTML authentication sessions that were connected to the victim’s machines and also used a printer spooler MSRPC interface that remotely executes the code on the machine worked.
These types of attacks are associated with man-in-the-middle attacks that are used to grant access to a network by manipulating the legal network and also create the authorized connection between client and server that was used to validate the authentication request while getting the network access.
These exploits are permitted the user to get the advisory to remotely execute the code on Windows OS and move on to another network to cause the critical system that includes server hosting, domain controllers that results indirectly compromising of NTLM credentials to the server.
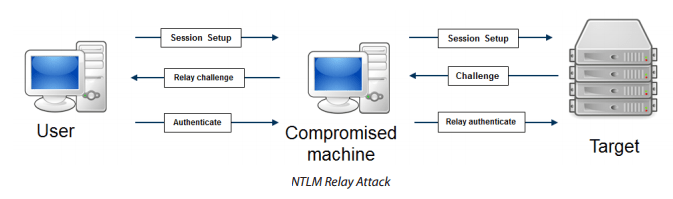
These types of attacks can be done by SMB and LDAP signing and turning on the EPA, CVE-2021-1678 exploits as the weakness in MSRPC that enables the vulnerability present and relay the attack.
Whereas the researcher found that the IremoteWindspoor is an RPC interface that assists in remote printing spooler management and can be used to access and execute the series of RPC operations and write the arbitrary files that target the machine that used intercepted NTLM sessions.
On the other hand, Microsoft in a support document said that this vulnerability is caused by increasing the RPC authentication level and introduce a new updated policy and registrary key that permits the customers to disable or enable the enforcement mode that presents on the server-side to increase the authentication level.
12th January Windows released an update, that deals with the company organizations to enable the enforcement mode on the print server. While setting it the expert says that it will enable in the Windows devices by 8 June 2021.



