Investigators have revealed sensitive weakness in well-known software applications that could be victimized to deactivate their security and manage allow-listed applications to execute vicious tasks on behalf of malware to destruct anti-ransomware defenses.
Similar attacks have been reported by academics from the University of Luxembourg and the University of London, are aimed at preventing the secured folder feature offered by antivirus programs to encode the files (aka “Cut-and-Mouse”) and exhaust their real-time security by resembling mouse “click” events (Aka “Ghost Control”).
“Antivirus software always provides high level of security, and they are important element in the everyday struggle against criminals,” said Prof: Gabriele Lenzini, chief scientist at the Interdisciplinary Center for Security, Reliability, and Trust at the University of Luxembourg. “But they are challenging with criminals who are now having much and more resources, power and devotions.”
While keeping them separately, defects in malware mitigation software could not just allow unauthorized code to turn off their security features, design errors in Secured Folders solution provided by antivirus vendors could be victims by, say, ransomware to change the items of the file using an app that has right to go through the folder and encode user data, or a wipeware to irrevocably damage personal files of users.
Secure folders permit the users to specify folders that need extra layer security to defeat destructive software, thereby probably block any unsafe access to your secured folder.
Why Trusted Applications?
“A small set of trusted applications is permitted privileges to write to secured folders,” researchers said. “However, trusted applications themselves are not secured from being misused by other applications. This faith is therefore unjustified since malware can execute operations on the secured folder by using trusted applications as intermediaries.
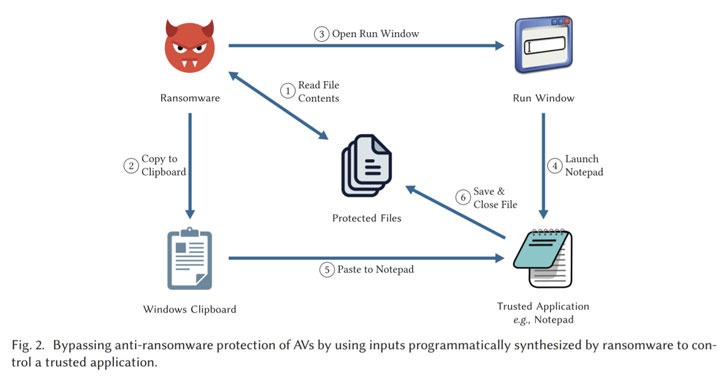
A scenario of attack is created by the researchers who discovered that malicious code could be utilized to manage whitelisted applications like Notepad to complete write operations and encode the victim’s file preserved in the secured folder. In the end, the ransomware goes through the files in the folders, encodes them in memory, and copies them to the system clipboard, by which the ransomware starts the Notepad to overwrite the contents of the folder with the clipboard content.
Even more, by leveraging Paint as a whitelisted application, the researchers discovered that the previous attack sequence could be utilized to overwrite user’s files with an aimless created image to damage them forever.
On the other hand, a Ghost Control attack could have serious drawbacks of its own, as turning off real-time malware protections by affecting appropriate users actions performed on the user side of an antivirus solution could allow an adversary to drop and run any crook program from a remote server under this control.
How Many Antivirus Discovered Vulnerably?
During the studies, 29 antivirus solutions evaluated from 14 of them were discovered vulnerable to the Ghost Control attack, while all the 29 antivirus programs tested were discovered to be at high risk from the Cut-and-Mouse attack. The investigators didn’t name the victims who are affected.

In case, the discoveries are a gesture that protection solutions that are specially designed to secure digital assets from malware attacks can experience weaknesses themselves, thus overwhelm their actual purpose. Even as antivirus software providers extend to proceed up defenses, malware authors have evaded past such barricades through the evasion and obfuscation tactic, not to acknowledge bypassing their observable detections using adversarial inputs by poisoning attacks.
“Protected compensability is a known concern in security engineering,” researchers said. “Elements that, when taken in isolation, offer a several known attack surface do create a wider surface when injected in to system. Components collaborate one another and with other parts of the system generated a dynamic with which an attacker can collaborate too and in ways that were not foreseen by the creators.”



