On Monday, Microsoft released a one-click mitigation tool that takes all the countermeasures required while controlling or securing these attacks that were spreading using the ProxyLogon Exchange Server attack.
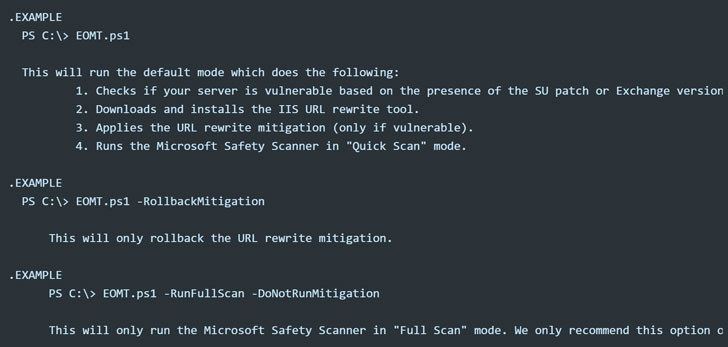
Microsoft named this tool as Exchange On-Premises Mitigation Tool (EOMT), which executes on PowerShell script and revokes the risk of attack that uses the CVE-2021-26855 and scans the Exchange Server with the help of Microsoft Safety Scanner feature that deployed the web shells and also attempts to remediate the detected compromises.
What Happened Next?
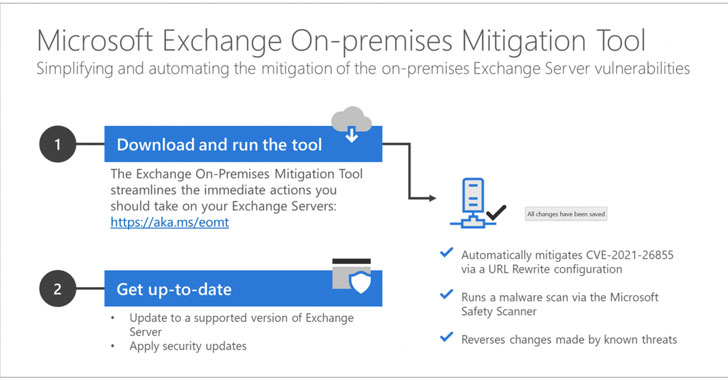
This updated and new tool is specially designed for the users who are still not aware and apply the updated patch given by Microsoft while controlling the effect of Exchange Attacks.
This software development was created for discriminating the attacks executing on the Exchange Servers that were located across the world and at the risk. However, multiple governments and other hacking groups are using the backdoors, ransomware, and miners that released the proof-of-concept while fueling these attacks.
According to the investigation of RiskIQ, 317269 out of 400,000 on-premises Exchange servers are patched under March 12 update, these servers are located in United States, Germany, Britain, France, Italy, and other countries.
Whereas the United States organization named as Cybersecurity and Infrastructure Security Agency (CISA) also updated its guidance and other seven variants of China Chopper web shell that has been penetrated by the attackers.
However, the web shell is getting popular as the attackers are executing the attacks using the post-exploitation tool.
The Experts are also addressing that Microsoft is also doing an investigation and seeking a solution to legitimate this attack that was detected in January and now spreading across the world and forces the organizations to release a security patch.
Several experts also shared that the investigators are focused on whether the organization shares the information about this vulnerability present in Microsoft Active Protections Program or it accidentally gets leaked to other groups.
Whereas the experts also claimed that, various tools are used in another wave of attacks that was executed at the end of February and they got the same PoC attack code that Microsoft is sharing with the antivirus organizations and also with other legal authorities on 23rd February, it may increase the possibility that the hackers may get the information from an insider that works in Microsoft or with other security partners.
Summering Up
Security experts also discovered that the attackers are using the same set of vulnerability which are used to conduct the previous attack that is associated with target networks and stealing mailboxes.
This is the second time in 4 months that nation-state attackers are involved in a cyberattack that potentially affects the business and other organizations. Microsoft also said that these vulnerabilities are executed by multiple hackers and criminal organizations that also deal with ransomware attacks and other potential attacks.



