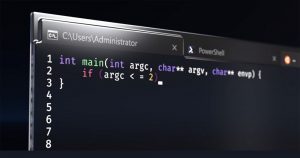
The security researcher discovered another email campaign that was initiated by the attackers while distributing the malware that was signed or written in Nim programming language.
What is Nim?
Nim is a statically typed and compiled programming language, it also combines the successful concepts from other mature languages like Python, Ada, and Modula. Whereas the hackers used this for making malware identified in the threat scene.
How this All Risen?
The main reason why these hackers choose a rare programming language, because they don’t want to detect easily as reverse engineers are not aware of these rare languages called Nim and they are also focused on developing the detection for it. However, some tools and sandboxes maybe struggle to analyze the samples of it.
Multiple organizations like Proofpoint are now tracking the operators from the campaign that works under the moniker TA800 and they also started distributing the NimzaLoader from 3rd February 2021, the latest activity TA800 is also used as BazaLoader from April 2020.
Whereas the APT28 is also linked while delivering the Zebrocy malware the also used the Nim-based loaders, the appearance of NimzaLoader is also the sign that the hackers are constantly using the new tools of malware to avoid unwanted detection.
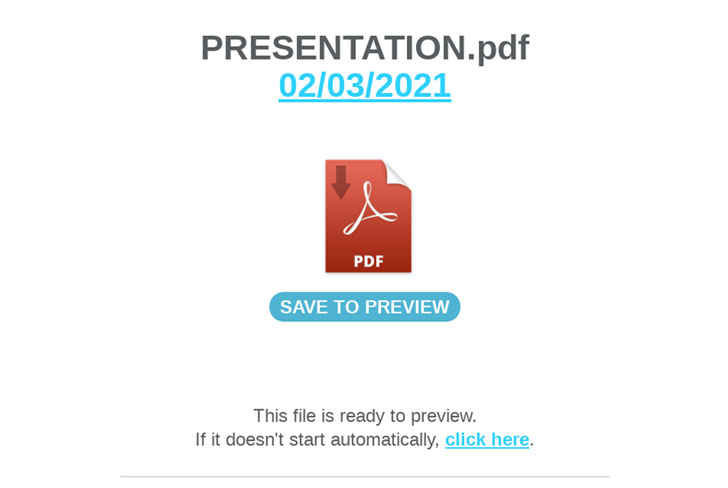
In the case of BazaLoader, another campaign was also spotted on 3rd Feb that steals the user’s personalized emails with phishing techniques that contains the link of PDF document that simply redirected the users to the NimzaLoader executable page that was created on Slack, which displays a fake Adobe icon and uses social engineering attacks tricks while infecting the users.
Once the users clicked on the malware, it will give the users data access to the hackers along with that the malware is capable to execute arbitrary commands that were retrieved from the C2 server and also deals with PowerShell commands execution, deploying additional malware, and injecting the shellcode into the running process.
Conclusion
Since the evidence founded by the law enforcement agencies also makes clear that NimzaLoader is also used while downloading and executing the Cobalt Strike as another payload and it also suggests the hackers targeted the users with the help of different tactics.
However, it is still unclear that if Nimzaloader is just a threat of the radar or it is some other attack, in case Nimzaloader will be operated by the attackers then they used the same way which was used by the BazaLaoder while spreading it.