Different Zyxel gadgets including firewalls and passageway (AP) regulators contain a hardcoded username-secret phrase mix in the firmware pictures, which has now been uncovered.
These qualifications put away in plaintext and noticeable to anybody with admittance to the firmware picture can give them manager admittance to the gadget by means of SSH, making this a genuine zero-day weakness.
Zyxel Communications is a Taiwan-based maker of systems administration gadgets, with workplaces around the globe. The $379 million organization utilizes more than 1,500 individuals around the world.

Which Firmware is Compromised?
Followed as CVE-2020-29583, the High severity weakness concerns cleartext capacity of touchy data inside Zyxel gadget firmware—for this situation, hardcoded ace secret phrase that can give director admittance to anybody by means of SSH.
As per Zyxel, the first motivation behind this undocumented secret key was to convey programmed updates to through FTP.
“This sposticated password vulnerability was discovered as ‘zyfwp’ client account in some Zyxel firewalls and AP regulators. The account was intended to convey programmed firmware updates to access point through FTP,” states Zyxel’s security warning.
An example web uncovered ZyXEL gadget running the weak firmware variant.
In any case, this additionally implies, enemies can distantly take advantage of the affected Zyxel firewalls and AP regulators with director advantages, whether or not some other client accounts with solid passwords exist on the gadget. This hardcoded qualification blend would fill in as a “master key,” or a secondary backdoor.
The bug was found and capably revealed a month ago by security analyst Niels Teusink, who delivered his discoveries, alongside the username zyfwp in a blog post, however redacted the hardcoded secret word.
Nonetheless, this week, security researcher dozer revealed the hardcoded passwood that includes: PrOw!aN_fXp
Devices Exposed and Fixed Now
More then 100000 devices are infected and patched now, “As SSL VPN on these gadgets works on a similar port as the web interface, a great deal of clients have uncovered port 443 of these gadgets to the web. Utilizing freely accessible information from Project Sonar, I had the option to distinguish about 3,000 Zyxel USG/ATP/VPN gadgets in the Netherlands. Internationally, more than 100,000 devices have uncovered their web interface to the web,” said Teusink in his blog entry.
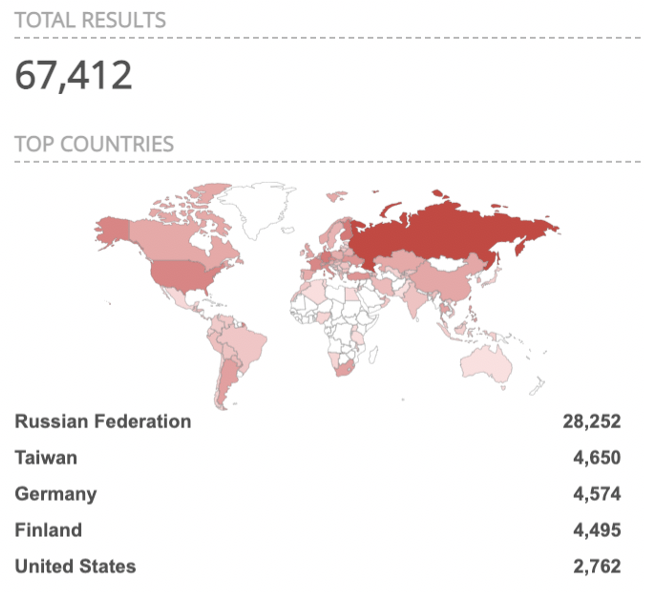
As seen by Security Report today, a huge number of Zyxel gadgets appear on IoT web indexes like Shodan. While not these uncovered gadgets may be weak to CVE-2020-29583, the finding focuses to an enormous Zyxel client base overall who might have conceivably been affected eventually by this zero-day.
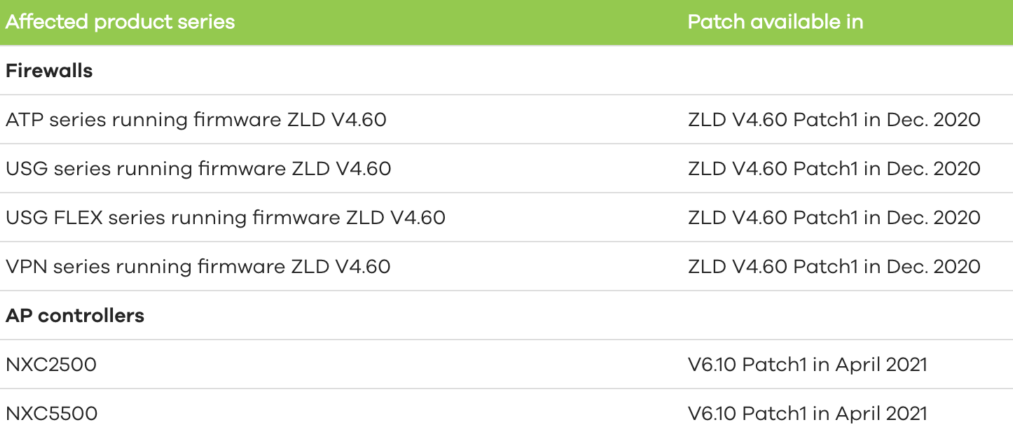
Zyxel has uncovered top notch of weak gadgets and fixed firmware forms accessible that administrators should overhaul their gadgets as well.
It is important that programmed updates may not generally be empowered on some Zyxel gadgets as a matter of course. Accordingly, framework overseers are encouraged to physically check if their Zyxel equipment is affected and apply the updates.
Disclosures like these strengthen security is as solid as its most vulnerable connection and that security by lack of clarity doesn’t work.
A hardcoded ace secret key in mission-basic systems administration gadgets delivers some other administrator certifications disputable, yet the secondary passage access can likewise be abused by country state entertainers to clandestinely lead their reconnaissance exercises under the radar.



