In this period of Covid-19 security is becoming the weakest point. Multiple organizations released updated security patches while making them more secured. However, Apple is also going to released the update for macOS while addressing the activated exploit and other zero-day vulnerability that may mislead the other security protections and authorized unprotected software that executed on Mac OS.
The vulnerability was identified as CVE-2021-30657 that reported by the security experts on 25th March. The expert also said that the unsigned, unnotarized, and script-based proof of concept would be reliable as the sidestep of all the macOS security mechanisms that are fully patched macOS systems and M1. These are loaded with the functions that return the target from infecting the macOS user.
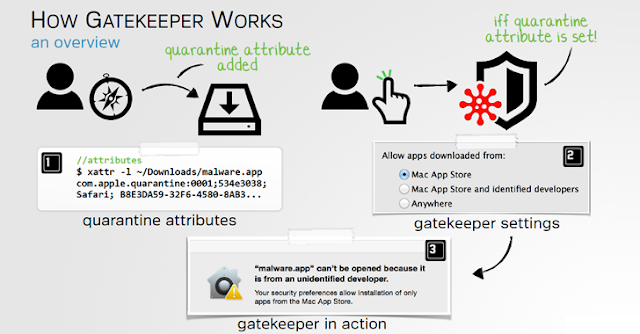
This feature is inbuilt in Apple macOS named as GateKeeper which permits the trusted applications while executing that applications having the authorized signature from the App Store or from the registered developer that was cleared about the automation process named as app notarization that examins the software for harmful content.
This newly discovered vulnerability enabled the craft and applications while revoking the Gatekeeper services and permits them to get executed without managing the security warnings. This entire operation deals with packaging the dangerous shell script with the double-clickable application feature so that the malware can be clicked double and run the applications.
However, it a type of application that you can double click, and the users of macOS also able to view the application from the menu and know the information about the payload itself.
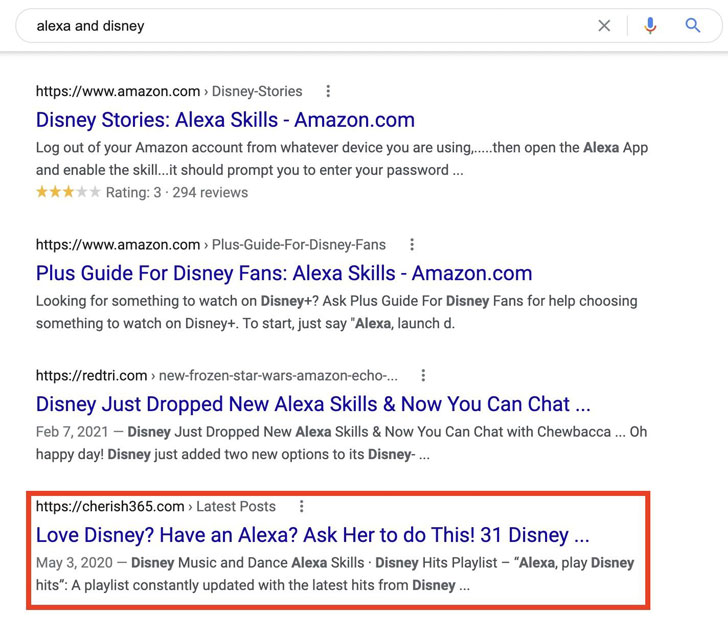
According to the security experts, the attackers who are working behind this attack will able to bypass the Gatekeeper vulnerability already on 9th January 2021. Although it distributed using a method named engine poisoning or spamdexing which identified in 30% of accounts linked with macOS.
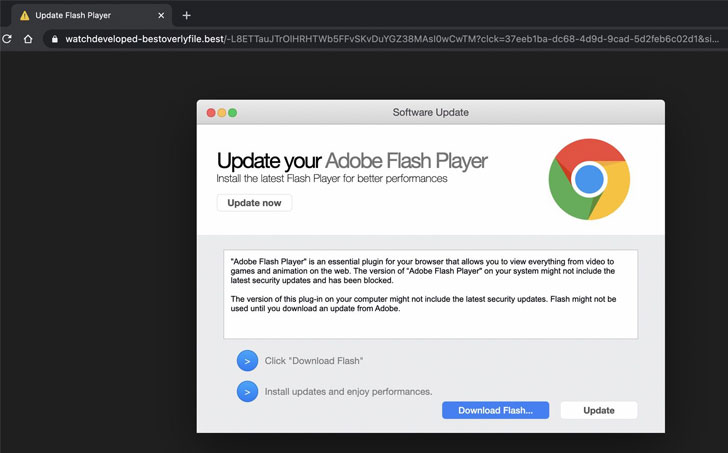
Whereas, the attacks that are overlapping the search engine results contain the malicious links, and these links redirect the users to the web page that downloads an application update which further used while executing the payload at another stage. This entire process may infect the whole system by executing more advanced threats that include data breaches and ransomware.
Since, the update delivered on Monday will also deal with these above-mentioned vulnerabilities or with another critical flaw named Webkit Storage identified as CVE-2021-30661 that has the capability to runs the arbitrary code in iOS, macOS, watchOS, and tvOS which access the maliciously crafted web content.
Although Apple is aware of these issues and takes the steps required. The organization also said that the security document and other issues are also addressed once they use-after-free the vulnerability and improved the memory management.
Summering Up
Apart from the updates the organization also released iCloud for Windows 12.3 which deals with the security patches of the 4 security issues present in WebKit and WebRTC with other that may permits the attackers to execute the Cross-Site scripting attacks that deals with CVE-2021-1825 and that infect the kernel memory as CVE-2020-7463.
The organization also advised the users to update the latest version while reducing the risk of associated flaws present.



