

































+
Years Experience
+
Customers
% +
Client Retention
M +
Identities Protected
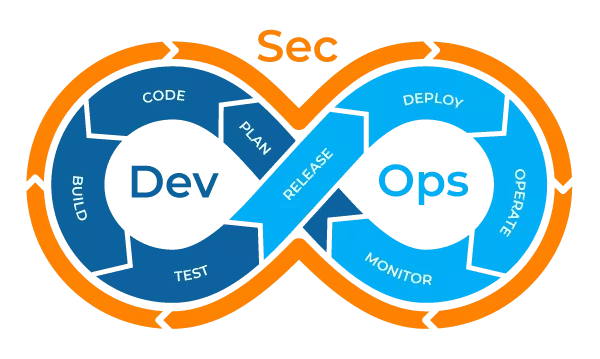
Secure DevOps or DevSecOps is a term coined which is frequently used to describe DevOps practices that encompass security tasks and critiques throughout the SDLC.
It is the modern-day strategy that discover security hassles early in the SDLC than after a product or feature is introduced. DevSecOps can decrease the bills concerned with fixing security flaws, with the aid of constructing security into each and every segment of the development process, from the prerequisite segment onwards. Privacy and security suggestions ought to be key to any company’s boom thru DevSecOps quality standards, and they should be backed at board level. Security ought to be characteristic of the SDLC process. Secure DevOps makes almost anyone responsible for security.
Secure DevOps Best Practices :
- Include cyber security professional as early as possible in the SDLC
- It is treasured to instruct developers about the attacker’s perspective, realistic hacking techniques and prone applications
- Integrating records security into agile development to totally impenetrable work flow at each stage of the SDLC.
- Coding the regulatory demands
- Coding security precept for better, secure and fundamentally correct architecture
- Incident management, root cause analysis ,Deployment of Red, blue and purple teams and promoting Bug Bounties
- Automation & Configuration managements
- Secure coding techniques right from the design stage
- Security tooling in CI/CD
- CI / CD for patching
- Application Auditing & Scanning
DevSecOps Business Benefits:
- Financial Impact: Cost minimization is attained with the aid of discovering and resolving safety hassles during the development tiers which also boosts the tempo of delivery.
- Fast restoration: Restoration price is upgraded in the situation of a security event by means of using layouts and pet/cattle strategy.
- Threat searching can forestall poor visibility, and so can possibly enhance sales – it is of course handy to promote a certain product or service.
- upgraded universal security by means of minimizing vulnerabilities, minimizing insecure defaults, and enhancing code exposure and automation thru the use of immutable infrastructure
- Keeping in step with the innovation that is swift to cybercrime via efficiently managing security auditing, monitoring, and notification systems.
- ‘Secure via design’ notion is certain through the use of automatic security code review, computerized application security testing, educating, and empowering developers to use impenetrable layout patterns.
- Everyone is responsible for security. DevSecOps encourages a tradition of openness and transparency, and does so from the earliest degrees of SDLC.
- The viable to evaluate one of a kind troubles which can be seen through everyone – DevSecOps enables a lifestyle of time-honored iterative advancements.
What We Deliver ?
It’s an important practice that gives organizations visibility into real-world threats to your security. As part of a routine security check, penetration tests allow you to find the gaps in your security before a hacker does by exploiting vulnerabilities and providing steps for remediation.
Digital Report
Our experts will furnish an itemized security evaluation report with legitimate remediation steps to be taken.
Distinguish Security Weaknesses inside your Digital Asset permitting you to proactively remediate any issues that emerge and improve your security act.
Vulnerability Data
Constantly updating Vulnerability Information to stay in touch with the emerging threat landscape.
Receive overview and trend data of all of the current security issues you face in your organisation. All viewable on an Digital Report.
Skilled Consultants
We also assured you that your assessments are executed by qualified experts.
Our group of security specialists holds industry capabilities, for example, CHECK Team Member and Team Leader, CEH, ECSA, OSCP, CISA, CISSP, and many more.
Why Xiarch ?
Xiarch is a CERT-IN Empanelled & ISO 9001:2015 | ISO 27001-2013 Licensed Cyber Security Company and IT Services Company with solutions providers in Information Security like VAPT Services, Penetration Testing Services, Vulnerability Assessment Services, Among our consumers we proudly work for Government Organizations, Fortune one thousand Companies and countless start-up companies. We are additionally Value Added Partners, Authorized Re-sellers & Distributor of Leading Web Application Security Testing Tools.
We are headquartered in Delhi and have branch presence in Gurugram and Mumbai - India
Contact our sales team @ +91-9667916333 for further clarifications on above stated service, you can also reach us by an email at [email protected]. We’ll be great full to serve you. Happy Security.
Few Customer Testimonials
Our clients like us for our specialized abilities, administration quality and polished methodology. Sharing their great words is a delight for us.
Trusted by Thousand of Brands











Get In Touch With Us
Test the effectiveness of your own security controls before malicious parties do it for you. Our security experts are here to help — schedule a call today.
Xiarch Security is an global security firm that educates clients, identifies security risks, informs intelligent business decisions, and enables you to reduce your attack surface digitally, physically and socially.
Certified Security Experts
Our security experts are exceptionally qualified and confirmed by CEH, ECSA, OSCP, CISA, CISSP, and numerous others.
Communication & Collaboration
After surveying the code our specialists shared the best answers to correct them. Our experts will communicate with you for any further implementations.
Research-Focused Approach
We hold industry-leading certifications and dedicate part of every day to research the latest exploit techniques to ensure our clients remain protected from evolving online attacks.
Free Remediation Testing
Once your team addresses remediation recommendations, Xiarch will schedule your retest at no additional charge.













